Hello dear friends, today we will start a new series based on Android penetration testing. We will go to analyze the diva application.
WHAT IS DIVA?
DIVA (Damn insecure and vulnerable App) is an App intentionally designed to be insecure. We are releasing the Android version of Diva. We thought it would be a nice way to start the year by contributing something to the security community. The aim of the App is to teach developers/QA/security professionals, flaws that are generally present in the Apps due poor or insecure coding practices. If you are reading this, you want to either learn App pentesting or secure coding and I sincerely hope that DIVA solves your purpose. So, sit back and enjoy the ride. You can download the apk tool from this link
Installation
For this series, we will gonna use gennymotion as a virtual device.
- adb devices -l
- adb connect 192.168.56.109:5555
- adb install diva-beta.apk
Fantastic we had installed the Diva app
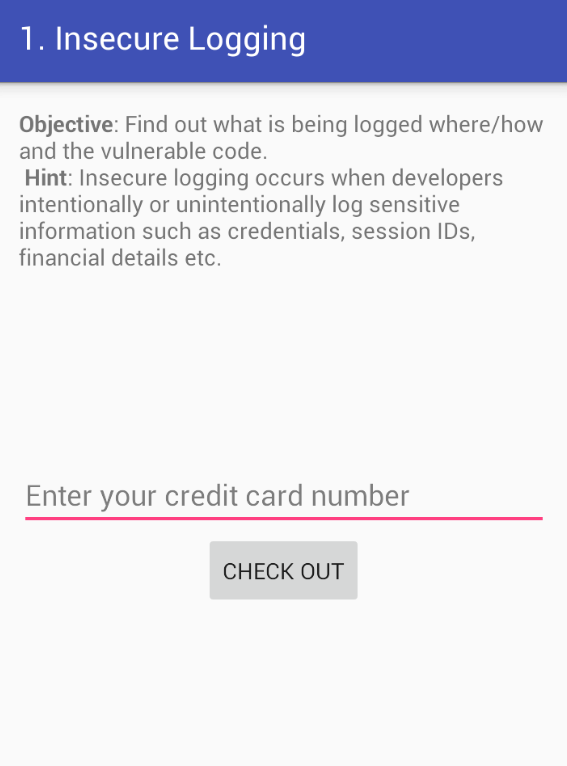
Insecure Logging
For this blog we will analyze the first exercise The insecure logging, but first at all what is the insecure logging? and why is dangerous? The “insecure logging” happens when developers log/print sensible info maybe for debugging purpose. A proper way to Log in Android is
[code lang=”swift”]
if (BuildingConfig.Debug) {
Log.i(TAG,"Message");
}
[/code]
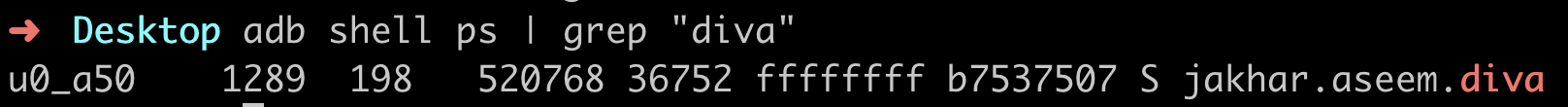
- get the process id: adb shell ps | grep “diva”
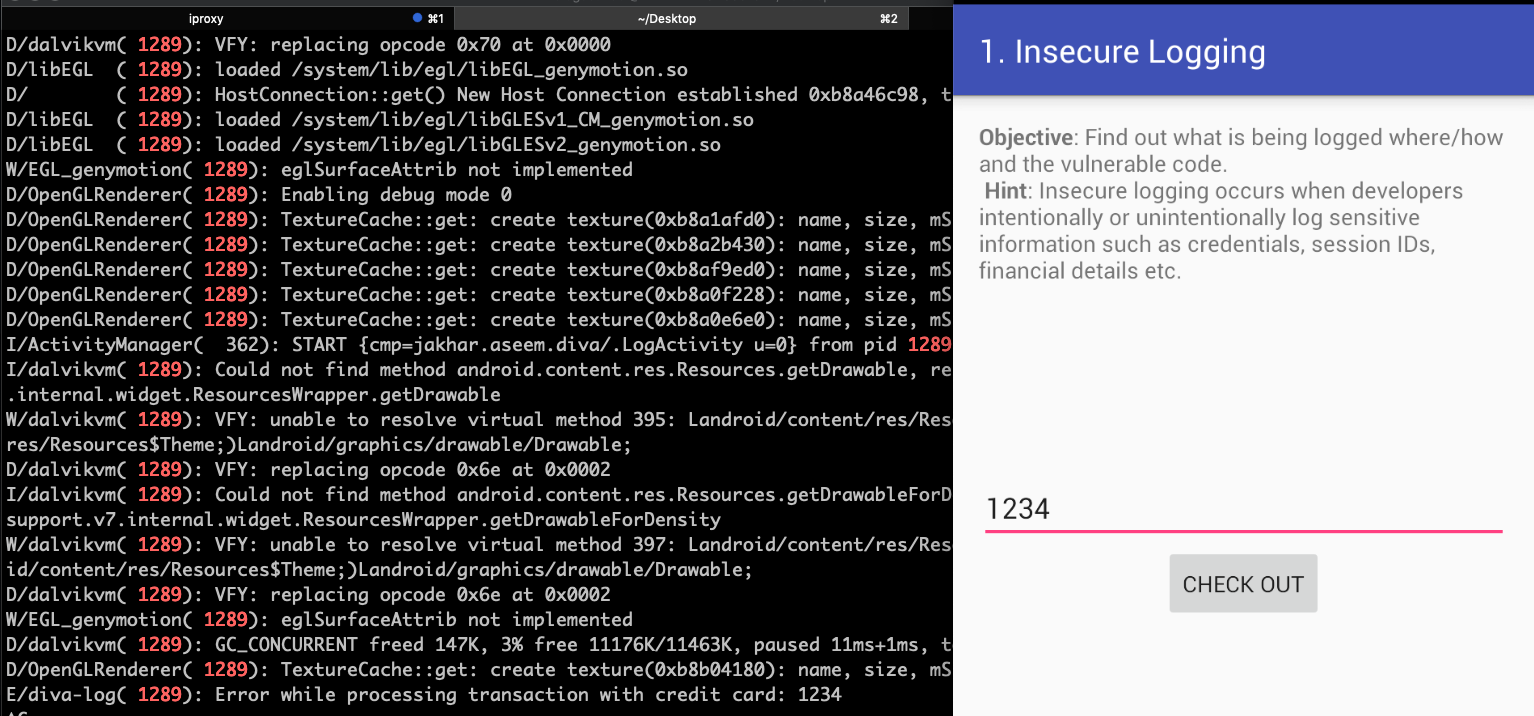
- Then we will use logcat tool for reading the logs adb logcat| grep -i 1289 (1289 is the pid)
Now type some “credit card” number into the text field and finally we will see the number into the logs
Fantastic we had completed the first exercise