Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve Fowsniff machine.
Description
This is a boot2root machine, It’s a beginner level, but requires more than just an exploitdb search or metasploit to run.
It was created in (and is intended to be used with) VirtualBox, and takes some extra configuration to set up in VMWare.
Information gathering
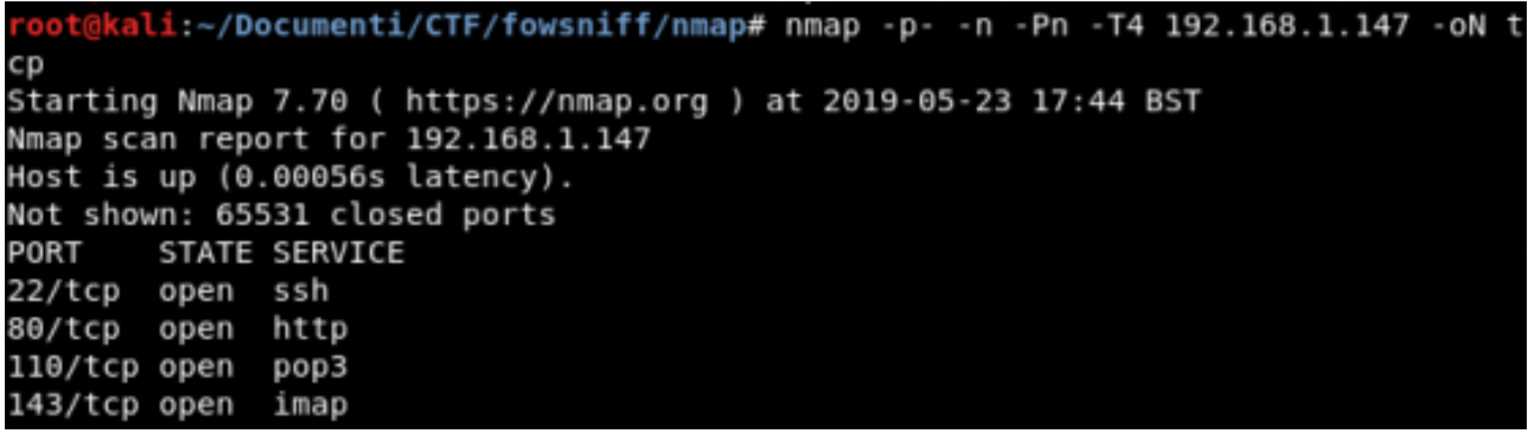
TCP Scanning
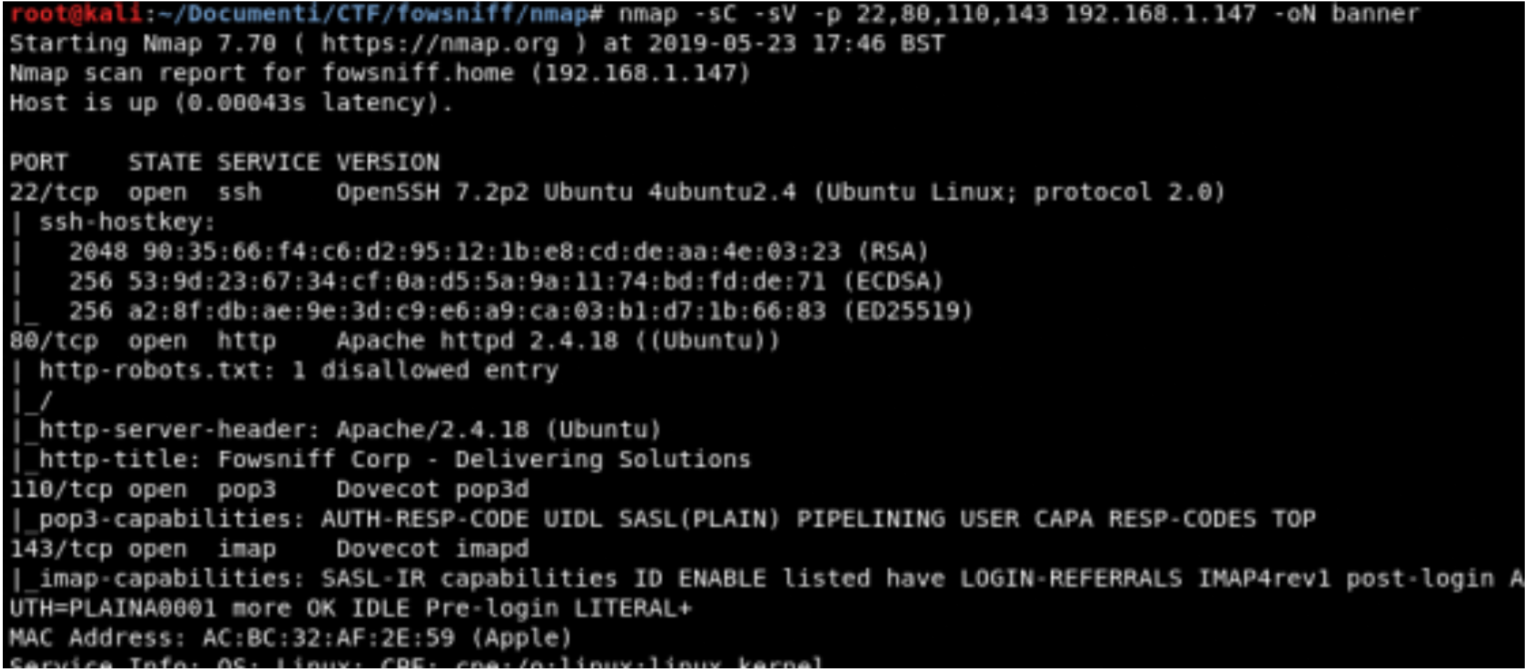
Banner Grabbing
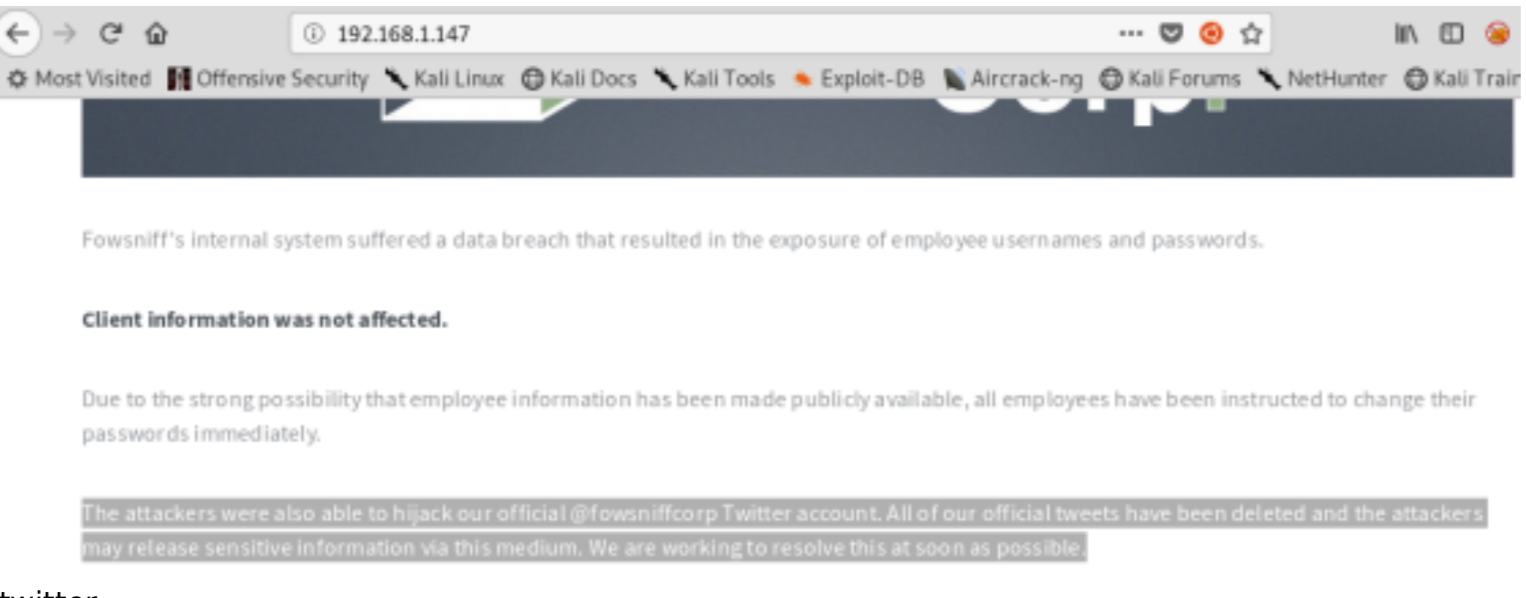
HTTP
On the home page, there is a fantastic hint
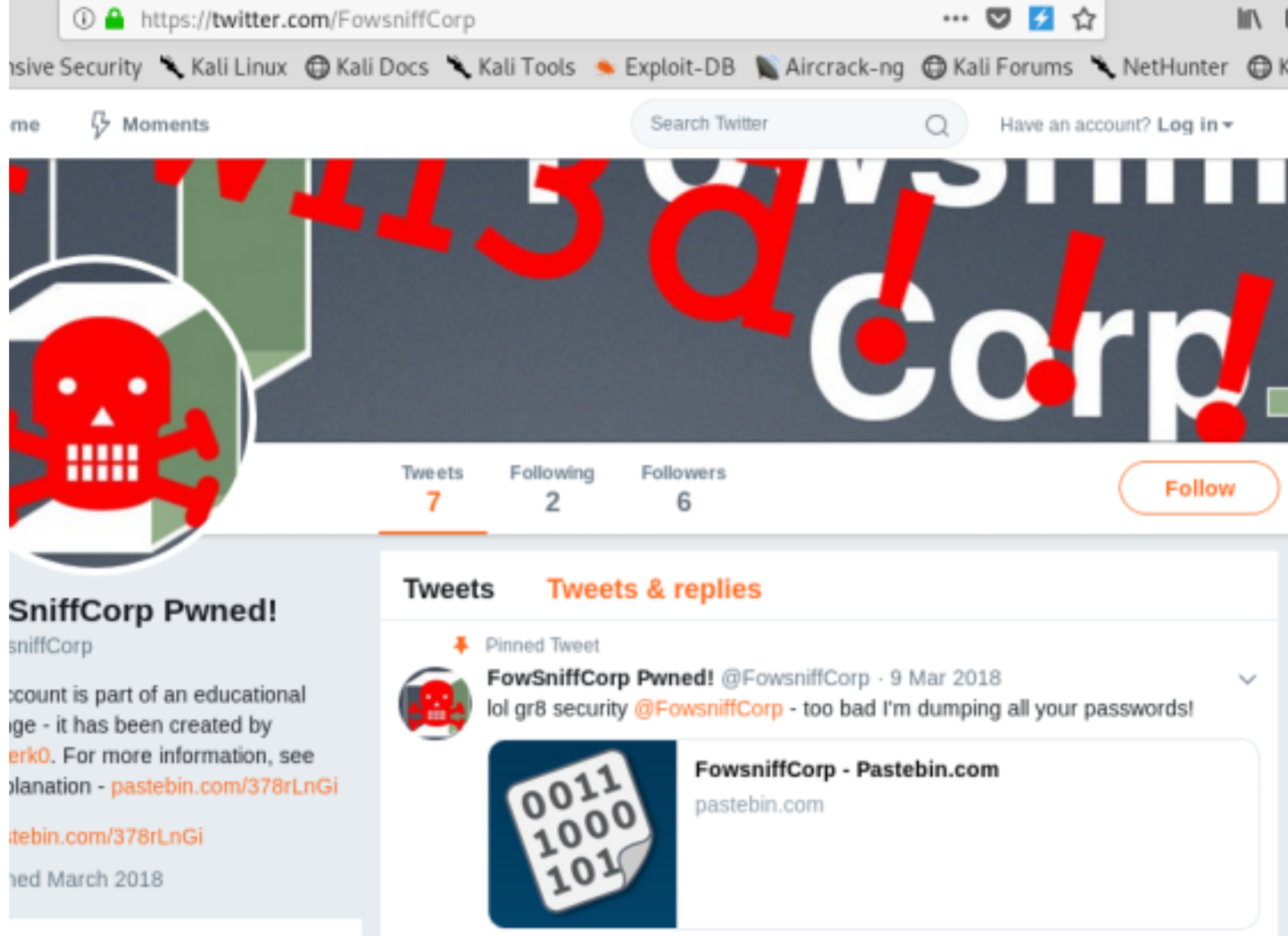
If we go on twitter https://twitter.com/fowsniffcorp/status/972208944285388800 we can find the “hacker” that post a link with the user’s credentials.
Crack the passwords
The next step is to crack the passwords:
mauer@fowsniff:8a28a94a588a95b80163709ab4313aa4 mustikka@fowsniff:ae1644dac5b77c0cf51e0d26ad6d7e56 tegel@fowsniff:1dc352435fecca338acfd4be10984009 baksteen@fowsniff:19f5af754c31f1e2651edde9250d69bb seina@fowsniff:90dc16d47114aa13671c697fd506cf26 stone@fowsniff:a92b8a29ef1183192e3d35187e0cfabd mursten@fowsniff:0e9588cb62f4b6f27e33d449e2ba0b3b parede@fowsniff:4d6e42f56e127803285a0a7649b5ab11 sciana@fowsniff:f7fd98d380735e859f8b2ffbbede5a7e
- john md5.txt –format=RAW-MD5 –wordlist=/usr/share/wordlists/rockyou.txt
Cracked password
Pop3
I use Thunderbird as mail client
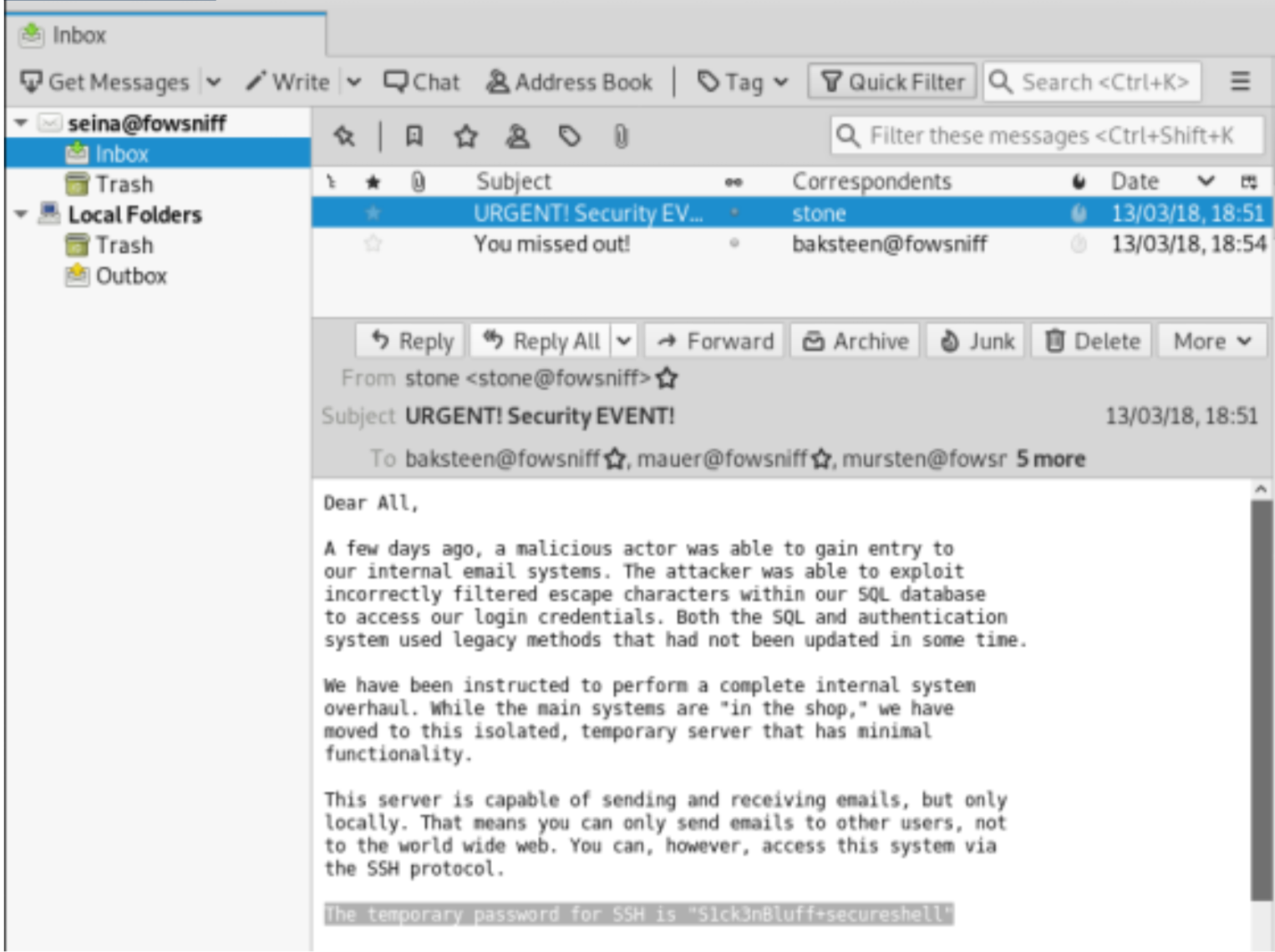
Fantastic we got ssh credential
SSH
- ssh baksteen@192.168.1.147
- password: S1ck3nBluff+secureshell
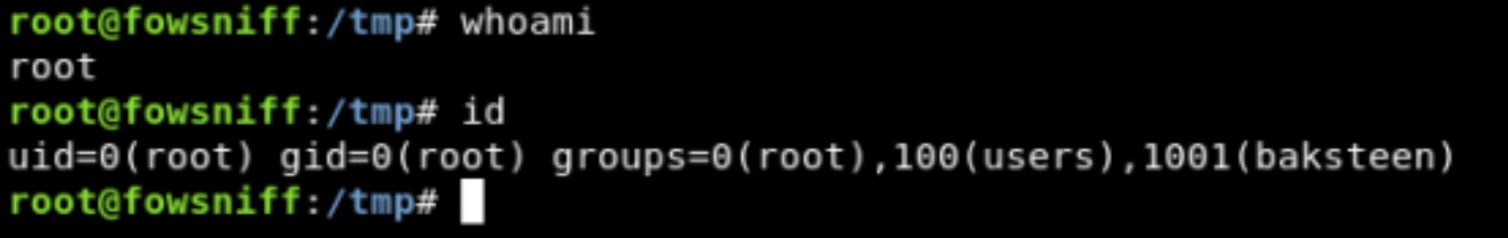
Privilege escalation
Fantastic this kernel version is vulnerable, you can find the exploit here.
Because the gcc is not installed on the target machine we have to compile the exploit on our machine
On our Machine