Greetings, everyone! In today’s blog, I’ll lead you through the process of bypassing jailbreak detection using LLDB.
Let’s explore LLDB, a crucial debugger in the realm of iOS development. Learn how LLDB equips developers to scrutinize and influence code execution during debugging, providing valuable insights into variables, registers, and more. Unearth useful tips and tricks to maximize the efficiency of LLDB for a smooth debugging experience in your iOS projects.
Installation on Jailbroken device
To begin, the initial step is to mount the iOS Developer Image. This can be accomplished using the following command. Please ensure to select the appropriate iOS version corresponding to your device; in my case, it’s version 14.5.
hdiutil attach /Applications/Xcode.app/Contents/Developer/Platforms/iPhoneOS.platform/DeviceSupport/14.5/DeveloperDiskImage.dmgExtract debugserver from the image to the current directory
cp /Volumes/DeveloperDiskImage/usr/bin/debugserver ./
Create an Entitlements.plist file as showed
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/ PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>com.apple.springboard.debugapplications</key> <true/>
<key>run-unsigned-code</key> <true/>
<key>get-task-allow</key> <true/>
<key>task_for_pid-allow</key> <true/>
</dict>
</plist>Sign debugserver
codesign -s - --entitlements entitlements.plist -f debugserverTransfer the signed binary to the /usr/bin/ directory within the iOS
scp debugserver root@{IP address of iOS device}:/usr/binChange the permissions to the binary
ssh root@{IP address of iOS device}
cd /usr/bin/
chmod +x debugserverExample of jailbreak detection bypass
The app that we will use is the following one link
In this instance, we will connect the debugger to the application and modify the return value of the method – [ViewController isCydiaAppInstalled]. Once the application is installed on the iOS device, it’s necessary to run the following commands:
On the first terminal we will connect to the iPhone via ssh
- iproxy 6666 6666 & iproxy 2222 44 & sleep 3 && ssh -p 2222 root@localhost
- cd /usr/bin
(before to execute the next command you need first lunch the application)
- debugserver localhost:6666 -a "JBDetectionOBJ"In a fresh terminal, execute the subsequent commands:
- lldb
- process connect connect://localhost:6666
Now we will set a breakpoint in the following way:
- breakpoint set --name "-[ViewController isCydiaAppInstalled]"
- cNow, engage with the app, press the button to activate the function, and halt the app at the breakpoint.

Now, type the command ‘s’ (step in) repeatedly until you reach the following point.

Using the command register read, we can inspect the registers.
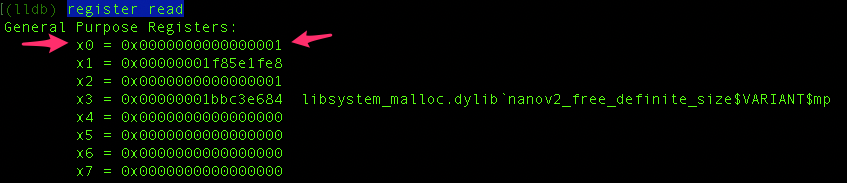
Our objective is to modify the value of register x0 from 1 to 0.
register write x0 0x0
continueIf the process proceeded successfully, you will encounter the following screen displaying a label indicating that the device is not jailbroken.