
Introduction
As the world of technology continues to evolve, businesses are increasingly adopting cloud services to streamline operations and enhance efficiency. Among the top cloud service providers, Amazon Web Services (AWS) has emerged as a frontrunner, offering a comprehensive suite of tools and services to cater to diverse business needs. However, with great power comes great responsibility, and security remains a top concern for organizations hosting their data on the cloud. AWS Penetration Testing has become an essential practice to safeguard cloud infrastructure and ensure data confidentiality, integrity, and availability.
AWS provides a comprehensive suite of cloud computing services that cater to a wide range of business needs. In this blog, we will dive into the various components of AWS and discover how they empower organizations to thrive in the cloud.
Amazon Elastic Compute Cloud (EC2):
Amazon EC2 is a foundational service that enables businesses to rent virtual servers, known as instances, in the cloud. These instances offer scalability and flexibility, allowing organizations to quickly scale their computing resources up or down as needed. With EC2, businesses can deploy applications, run batch processing, and handle high-performance computing tasks effortlessly.
AWS Lambda:
AWS Lambda is a game-changer for serverless computing. With Lambda, developers can execute code without the need to manage servers. It automatically scales based on the incoming request volume, ensuring optimal performance and cost efficiency. This service revolutionized application development by simplifying the deployment process and accelerating time-to-market.
Amazon Simple Storage Service (S3):
AWS S3 is a highly scalable and reliable object storage service. It serves as a vast data repository, allowing users to store and retrieve any amount of data from anywhere on the web. From media files to backup archives, S3 ensures high durability, availability, and security, making it an ideal solution for data storage needs.
AWS Identity and Access Management (IAM):
IAM is a critical component for securing AWS resources. It allows administrators to manage user access, permissions, and credentials. IAM ensures that only authorized users can interact with specific AWS resources, reducing the risk of unauthorized access and data breaches.
While Amazon offers a wide array of other services, the ones mentioned above are the ones we will focus on in these blogs.
Lab setup
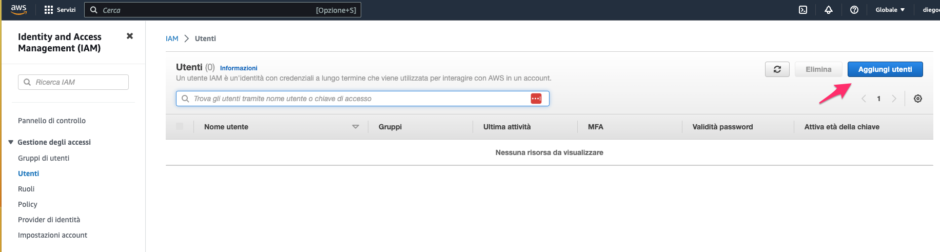
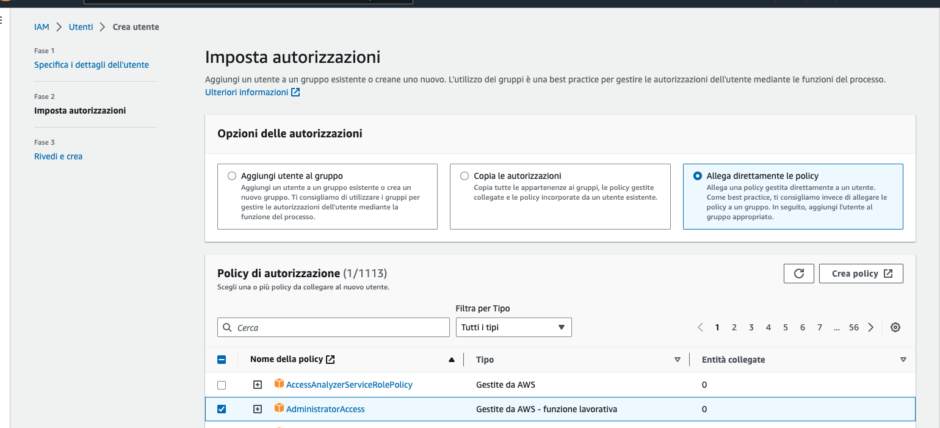
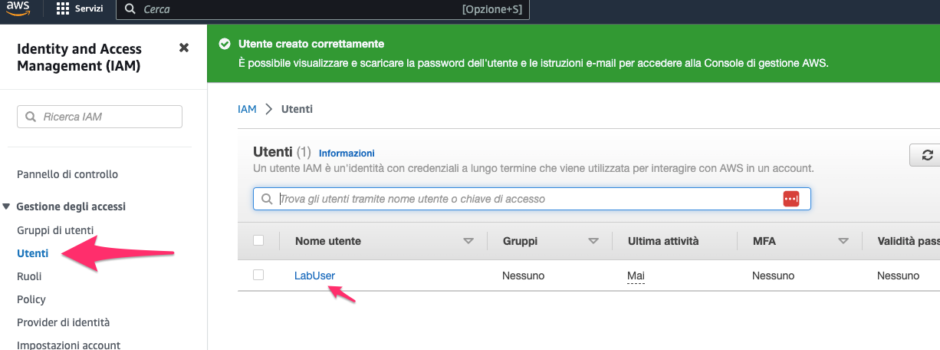
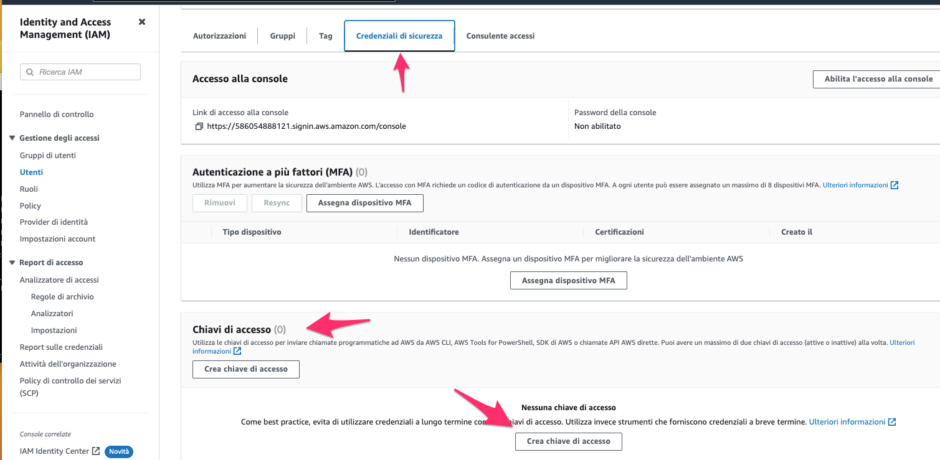
Firstly, we need to create an AWS account on Amazon. To do this, we must visit the following web address and follow the instructions. Next, we need to create a new user and grant them root privileges to build our lab.
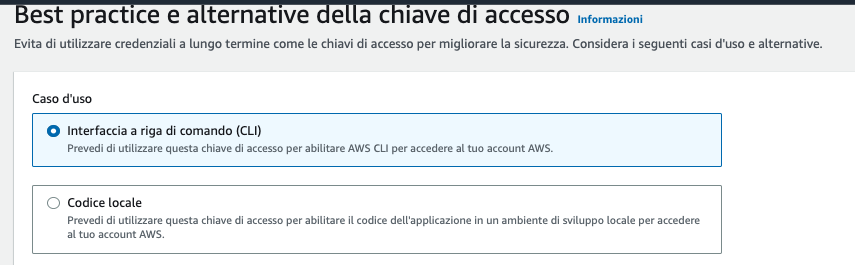
Install CloudGoat
CloudGoat is Rhino Security Labs’ “Vulnerable by Design” AWS deployment tool.

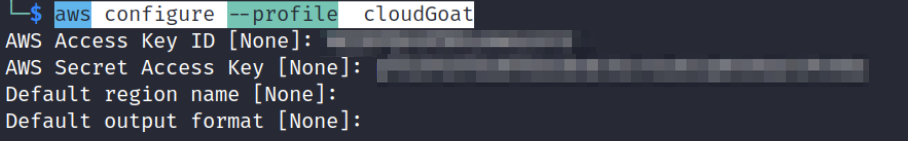
To set up our user in the AWS CLI on Kali, we need to use the following command.
aws configure –profile cloudGoat
To ensure Cloud Goat functions properly, the installation of Terraform is required. You can check if it is possible to install Terraform from the following URL
https://developer.hashicorp.com/terraform/downloads
Now, proceed with executing the following commands for the installation:
- cd /opt
- git clone https://github.com/RhinoSecurityLabs/cloudgoat
- cd cloudgoat
- pip install -r requirements.txt
After that, we need to cofigure the cloudGoat
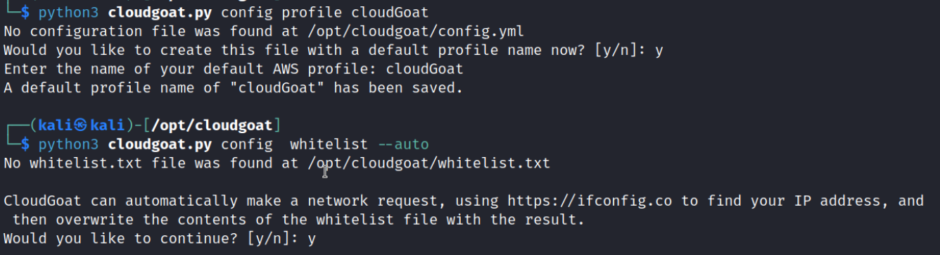
Install Pacu
Pacu is an open-source AWS exploitation framework, designed for offensive security testing against cloud environments. Created and maintained by Rhino Security Labs, Pacu allows penetration testers to exploit configuration flaws within an AWS account, using modules to easily expand its functionality. Current modules enable a range of attacks, including user privilege escalation, backdooring of IAM users, attacking vulnerable Lambda functions, and much more.
pip3 install -U pacu
In the upcoming blog, we will explore various scenarios and demonstrate how to exploit certain AWS services.