Tag Archives: Sicurezza Informatica
Android Diva Series: Insecure Data Storage Part 1

Hello dear friends and welcome back for another Android Diva series blog, today we will resolve Insecure Data Storage Part 1. For this exercise, we will use adb, first at all fill the text fields after that connect adb to the device adb connect ip get a shell adb… Read more »
Android Diva Series: Installation and Insecure log exercise

Hello dear friends, today we will start a new series based on Android penetration testing. We will go to analyze the diva application. WHAT IS DIVA? DIVA (Damn insecure and vulnerable App) is an App intentionally designed to be insecure. We are releasing the Android version of Diva. We thought… Read more »
Inject Frida inside an ipa file

Hello dear friends and welcome back for another mobile security blog, today I’ll show you how to inject frida inside an ipa application. So for todo that we need to install some tools: iOS Deploy brew install node npm install -g ios-deploy If you want to know more about this… Read more »
Frida: Demo 1 How to Hack an Android Application

Hello dear friends, and welcome back for another mobile application security blog, today I’ll show you how to bypass a login form with Frida. For this exercise, I did prepare an easy android Application that you can download from this link. After the download run the app on gennymotion emulator…. Read more »
CTF Vulnhub: Hackme 1 Walkthrough

Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve hackme: 1machine. Description ‘hackme’ is a beginner difficulty level box. The goal is to gain limited privilege access via web vulnerabilities and subsequently, privilege escalate as root. The lab was created to mimic the real-life environment. ‘hackme’… Read more »
How to install Frida on iOS device without Jailbreak

Hello dear friends, today I’ll show you how to “install” frida on iOS device without Jailbreak it, but first of the thing what is frida? Frida it’s a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript or your own library into native apps. The first step is… Read more »
CTF: DC-3 Walkthrough

Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve DC-3 machine. Description DC-3 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. As with the previous DC releases, this one is designed with beginners in mind, although this… Read more »
CTF: LazySysAdmin Walkthrough

Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve LazySysAdmin machine. Description Difficulty: Beginner – Intermediate Boot2root created out of frustration from failing my first OSCP exam attempt. Information gathering TCP Scanning Banner Grabbing Nmap scanning Dirb When the samba server is running it’s always a good… Read more »
CTF: bulldog Walkthrough
Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve bulldog machine. Description Bulldog Industries recently had its website defaced and owned by the malicious German Shepherd Hack Team. Could this mean there are more vulnerabilities to exploit? Why don’t you find out? 🙂 This is a standard… Read more »
CTF: DerpNStink Walkthrough

Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve DerpNStink machine Description: Mr. Derp and Uncle Stinky are two system administrators who are starting their own company, DerpNStink. Instead of hiring qualified professionals to build up their IT landscape, they decided to hack together their own… Read more »
CTF: FristiLeaks Walkthrough

Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve FristiLeaks. Description A small VM made for a Dutch informal hacker meetup called Fristileaks. Meant to be broken in a few hours without requiring debuggers, reverse engineering, etc.. Information gathering TCP Scanning Analyze the web app After… Read more »
Utilizzare il modulo shodan di metasploit

Ciao a tutti cari amici di iProg, oggi vorrei parlarvi di un modulo di metasploit ovvero shodan_search, in pratica questo modulo utilizza le api di shodan per permetterci di effettuare ricerche direttamente da metasploit. Per chi non lo sapesse shodan è un motore di ricerca, molto spesso viene anche chiamato… Read more »
mitmf Man in the middle
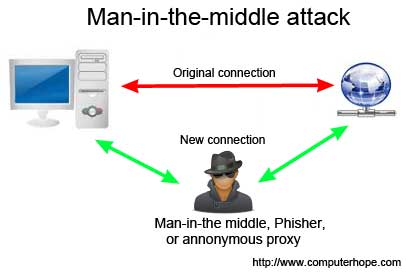
Ciao a tutti cari amici di iProg era da parecchio che non scrivevo un articolo, ma purtroppo sono stato molto occupato in questo periodo. Qualche tempo fa vi accennai in cosa consiste un attacco di tipo man in the middle, oggi vorrei mostrarvi un tool straordinario che si chiama mitmf ed… Read more »
Sicurezza Informatica: Introduzione

Tempo fa all’università ho seguito un corso sulla sicurezza informatica ed è stato veramente molto interessante, così ho deciso di approfondire l’argomento. Tengo a precisare che non sono un esperto in questo settore ma trovo che sia una cosa interessante condividere quello che ho imparato con voi. Cos’è la sicurezza informatica?… Read more »