In today’s blog, I want to introduce you to the concept of fuzzing and explain why it is important. The fuzzing process is quite straightforward—it focuses on randomizing input data and monitoring how the software responds to these inputs.
- Blackbox Fuzzing: This is typically used by attackers who do not have access to the source code. It focuses on input and output behavior, but its limitation lies in code coverage. Without full access to the codebase, it cannot test all possible execution paths.
- Whitebox Fuzzing: With access to the source code, testers can identify all potential injection points and thoroughly evaluate them.
- Graybox Fuzzing: This approach uses partial knowledge of the software, often obtained through tools like disassemblers, code coverage data, or debugging information.
Input Generation in Fuzzing: Key Approaches
The way input data is generated plays a crucial role in fuzzing. There are three main methods for generating input data:
Random Generation: Inputs are generated completely at random, without any prior knowledge of valid structures.
Mutation-Based Generation: This approach takes valid inputs and mutates them by introducing random changes. For example:
Valid Input: password
Mutated Input: pAszw’rd
Generation-Based Input: Inputs are created from scratch but follow the correct syntax or structure expected by the target application.
Once the inputs are generated and executed by the fuzzer, it monitors for potential errors such as segmentation faults, memory leaks, and other unexpected behaviors that could indicate security vulnerabilities.
Fuzzing in Action: Practical Example with AFL++ and Honggfuzz
You could write an entire book or even multiple on how to leverage this powerful technique for both developers and security researchers. Topics like integrating fuzzing into the CI/CD pipeline are essential for improving software security.
However, in today’s blog, I want to focus on a practical example and show you how to use two well-known open-source fuzzing tools: AFL++ and Honggfuzz. Let’s dive into how these tools work and how you can start using them to discover vulnerabilities in your applications.
Installing AFL++
1. Install Dependencies
Before installing AFL++, make sure your system has the necessary dependencies:
sudo apt update && sudo apt install -y build-essential clang llvm python3 git
2. Clone the AFL++ Repository
Download AFL++ from its official GitHub repository:
git clone https://github.com/AFLplusplus/AFLplusplus.git
cd AFLplusplus
make
Installing Honggfuzz
Honggfuzz is a modern, high-performance fuzzing tool used for security testing and bug discovery. Below are the steps to install it on a Linux system.
1. Install Dependencies
sudo apt update && sudo apt install -y build-essential clang llvm lldb python3 git
2. Download Honggfuzz from its official GitHub repository:
git clone –depth 1 https://github.com/google/honggfuzz.git
cd honggfuzz
make
At this point, we need a binary to test. For our first example, we will use AFL++, as it works exceptionally well when the source code is available. AFL++ allows easy instrumentation of the application, enabling more effective fuzzing.
Here’s a simple C program for our demonstration:
// test.c
#include <stdio.h>
#include <string.h>
void vulnerable_function(char *input) {
char buffer[64];
strcpy(buffer, input); // Vulnerabilità: copia senza controllo della lunghezza
}
int main(int argc, char **argv) {
if (argc != 2) {
printf("Usage: %s <input>\n", argv[0]);
return 1;
}
vulnerable_function(argv[1]);
printf("Program finished\n");
return 0;
}
Creating a Harness for Fuzzing
Before we proceed with fuzzing, we need to create a harness. A fuzzing harness is essentially a wrapper that prepares the target program for effective fuzzing. It ensures that the fuzzer can easily interact with the program by handling input in a way that maximizes coverage and efficiency.
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h> // Includi questa libreria per execlp
int main(int argc, char **argv) {
// Verifica che ci sia almeno un argomento passato (il percorso del file di input)
if (argc < 2) {
fprintf(stderr, "Usage: %s <fuzz_input_file>\n", argv[0]);
return 1;
}
// Prendi il percorso del file passato come argomento
char *file_path = argv[1];
// Apre il file in modalità lettura
FILE *file = fopen(file_path, "r");
if (file == NULL) {
perror("Errore nell'aprire il file");
return 1;
}
// Determina la dimensione del file per allocare abbastanza spazio
fseek(file, 0, SEEK_END);
long file_size = ftell(file);
fseek(file, 0, SEEK_SET);
// Alloca memoria per contenere il contenuto del file
char *fuzz_input = (char *)malloc(file_size + 1);
if (fuzz_input == NULL) {
perror("Errore nell'allocare memoria");
fclose(file);
return 1;
}
// Leggi il contenuto del file
fread(fuzz_input, 1, file_size, file);
fuzz_input[file_size] = '\0'; // Aggiungi il terminatore di stringa
// Chiudi il file
fclose(file);
// Stampa il comando che verrà eseguito con il contenuto del file
printf("Eseguendo il comando: ./test %s\n", fuzz_input);
// Esegui il programma con il contenuto del file come argomento
execlp("./test", "./test", fuzz_input, (char *)NULL);
// Se execlp fallisce, stampa un errore
perror("execlp failed");
free(fuzz_input);
return 1;
}Preparation
Before we begin the fuzzing process, we need to follow a few important setup steps. These steps involve creating directories for input and output, preparing the initial test file, and compiling both the fuzzing wrapper and the target program with AFL++.
We will create two directories: one for the input files and another for the output files (where the results of the fuzzing process will be stored).
mkdir in
mkdir outWe need to provide an initial input file for AFL++ to start the fuzzing process. We can start by creating a simple file that contains a string of characters.
echo “AAAAAA” > in/test.txt
This file will be used by AFL++ to begin the fuzzing with an initial value.
Now, we need to compile the fuzzing wrapper (which handles input redirection) and the target program using afl-gcc, which is the AFL++-specific GCC wrapper.
afl-gcc fuzz_wrapper.c -o fuzz_wrapper
afl-gcc test.c -o test
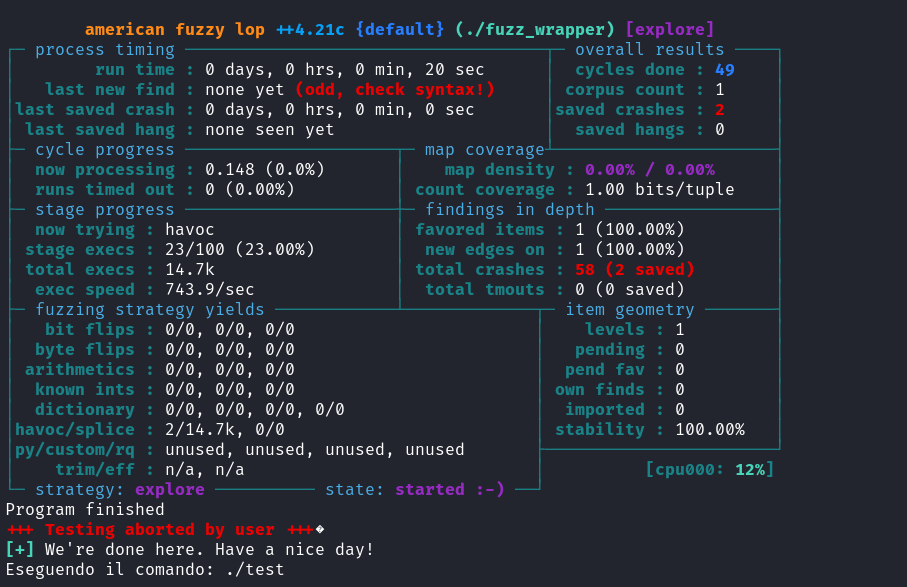
afl-fuzz -i /home/kali/Desktop/in -o /home/kali/Desktop/out -- ./fuzz_wrapper @@
Once you run this command, AFL++ will start generating new inputs, feeding them into your program, and monitoring the output for any crashes or unexpected behavior. The results will be saved in the out directory for later analysis.
Using Honggfuzz: Fuzzing a Binary Without Source Code
For the second part of this demonstration, we’ll use Honggfuzz to fuzz the target program. In this case, we will assume we only have the binary to analyze, not the source code.
gcc test.c -o test
gcc wrapper.c -o wrapperPlease note that we are using GCC and simulating a scenario where the source code is unavailable.
Finally, we can start fuzzing using Honggfuzz. The command below will execute the fuzzing process:
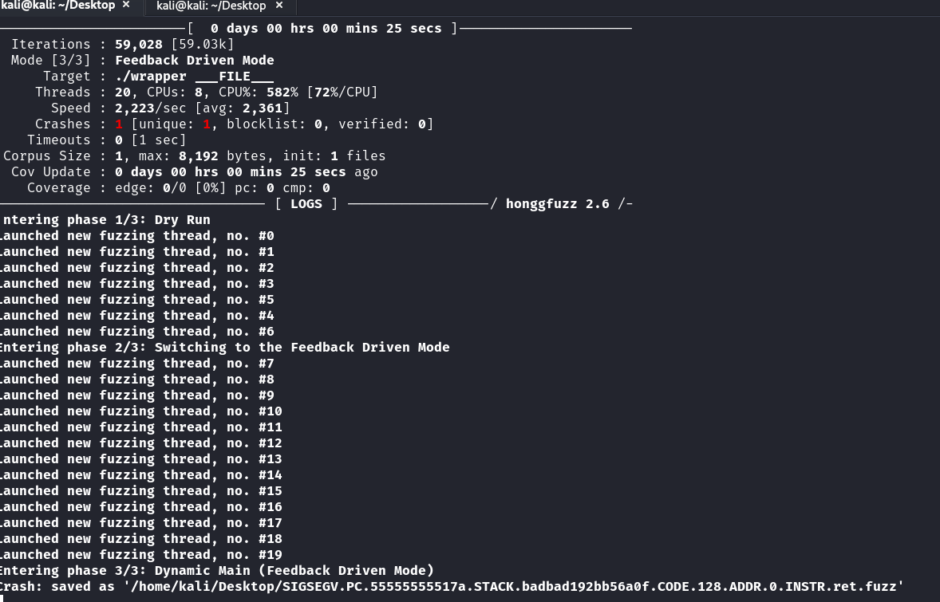
honggfuzz -i in/ -o out -n 20 -- ./wrapper ___FILE___
Once fuzzing has run for some time, you can analyze the results in the out/ directory. Honggfuzz will generate reports of any crashes or errors it has encountered during the fuzzing process. You can inspect the output files to investigate and fix any potential vulnerabilities.
In the next blog, we will analyze the crash. If you enjoy this type of content, please let me know!